- A new Python-based remote access trojan called PyVil has been added to Evilnum’s arsenal.
- The custom malware can take screenshots, run cmd commands, and download additional modules.
- Evilnum has also expanded its C2 infrastructure with additional domains, minimizing suspension risks.
The “Evilnum” group of actors has been pretty active during the past two years, and it appears that they are now going through major shifts in their toolset. The Cybereason Nocturnus team of researchers has been following them closely, and they report the emergence of a new RAT (remote access trojan) called “PyVil.” In addition to this custom tool, Evilnum is now using LaZagne as well, which helps them steal user credentials.
Evilnum is interested in UK and EU-based banks and financial organizations in general, which hasn’t changed. The group’s main goal is to spy its targets and try to exfiltrate sensitive data like VPN passwords, browser cookies, email credentials, and classified documents.
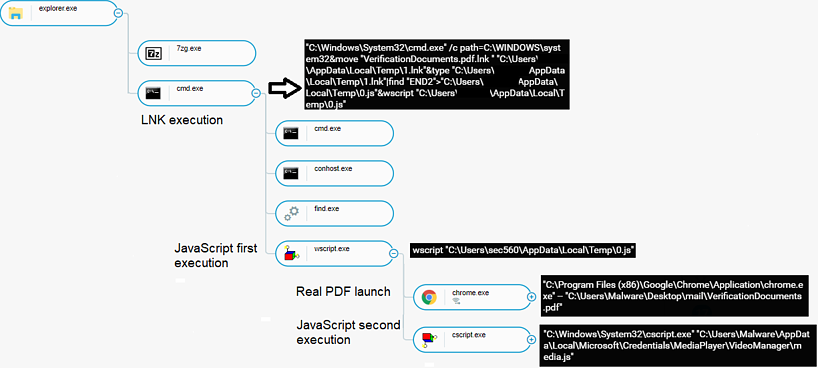
The infection chain is now differentiating from what used to be typical in the past, and the actors are now using a single LNK file that poses as a utility bill or driver’s license PDF. This file activates a JavaScript dropper, which sets up a scheduled task to retrieve the malicious binaries.
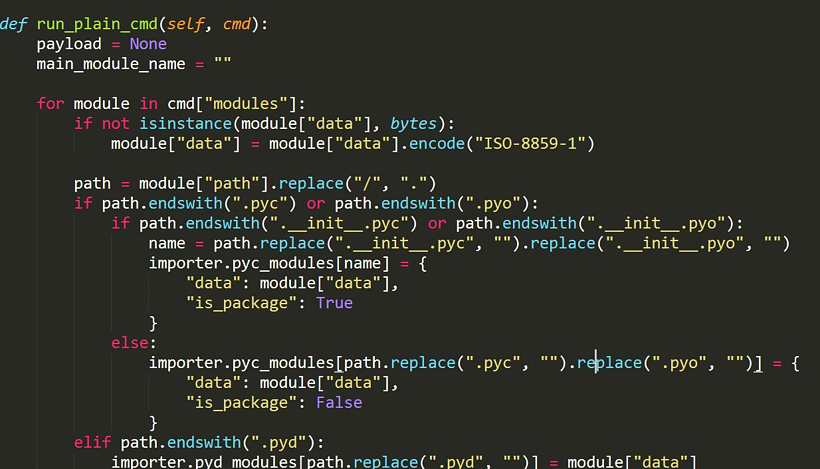
The new payload is the PyVil RAT written in Python, which is obfuscated with extra layers to make its decompilation hard.
The Nocturnus researchers used memory dumps to do it anyway, so they report the following functionality in the PyVil’s code:
- Keylogger
- Running cmd commands
- Taking screenshots
- Downloading more Python scripts for additional functionality
- Dropping and uploading executables
- Opening an SSH shell
- Collecting information such as what Anti-virus products are installed, which USB devices connected, or the Chrome version
When the RAT needs to phone back home to the C2, it does so via POST HTTP requests that feature RC4 encryption applied thanks to a hardcoded base64 key. In several recorded cases, PyVil RAT received a new Python module from the C2, which was basically a custom version of the LaZagne credential stealer.
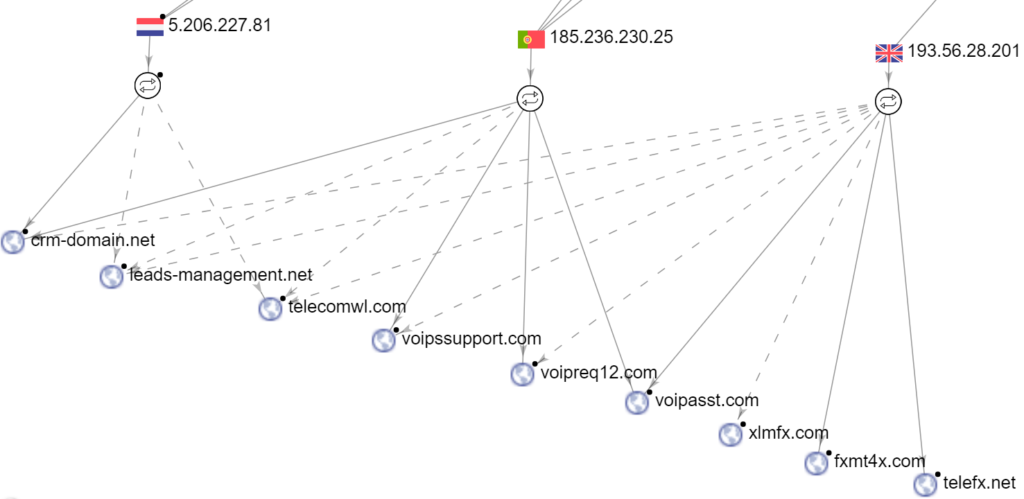
Finally, the infrastructure that supports the Evilnum operations seems to have grown significantly over the past couple of weeks, and so has the number of domain IP addresses associated with the group. This is indicative of the group’s goal to continue its malicious operations and actually up their game by deploying new tools and making sure that they are still able to remain undetected.
If you are among the potential targets, check out the full list of compromise indicators that could be enriched soon.
To read the original article:
https://www.technadu.com/evilnum-group-deploying-new-rat-pyvil/192272/