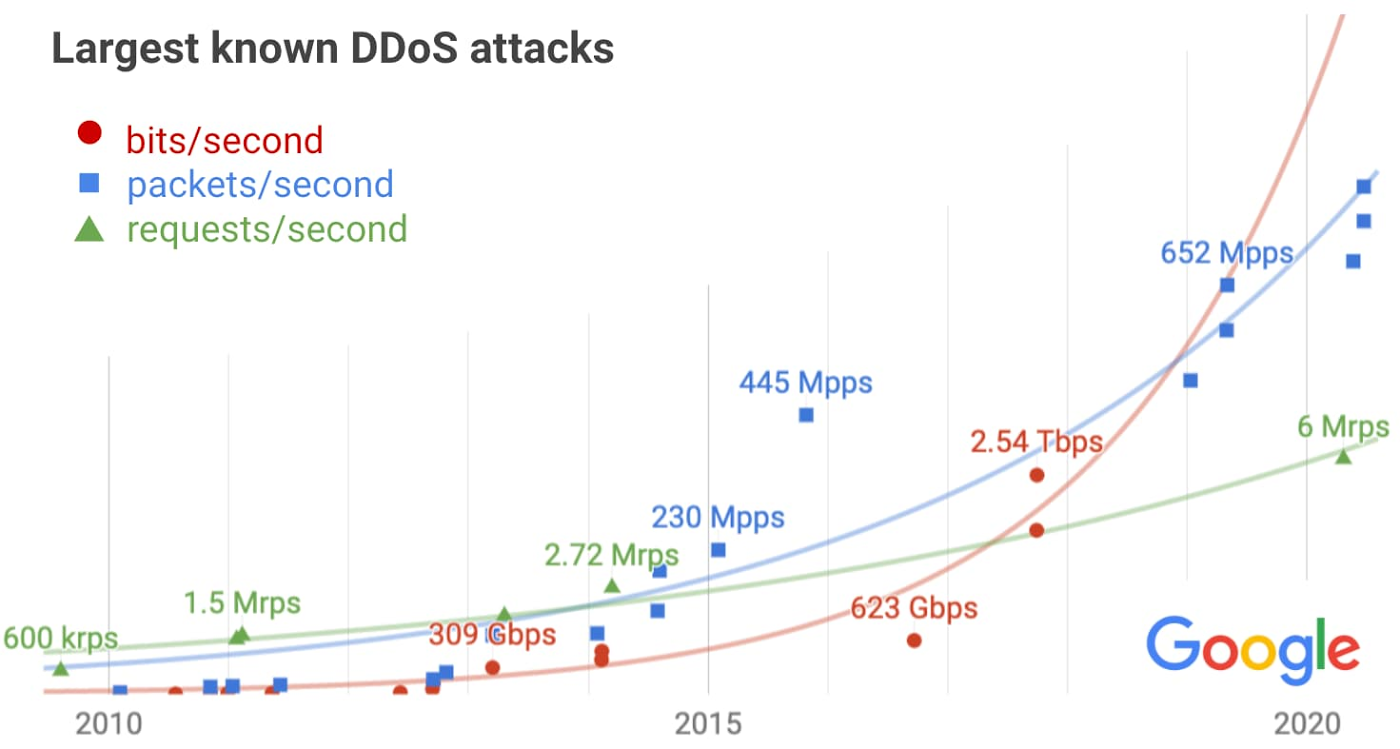
In an overview of distributed denial-of-service (DDoS) trends targeting its network links, Google revealed that in 2017 a nation-state actor used massive firepower that amounted to more than 2.54 terabits per second.
The actor targeted thousands of Google IP addresses at the same time and used several attack methods in a campaign that span across multiple months.
Google did not attribute the attack to a particular actor but said that the bad UDP packets hurled at its systems came from devices using several Chinese internet service providers (ASNs 4134, 4837, 58453, and 9394).
In an analysis of DDoS trends over the last years, Damian Menscher, a Security Reliability Engineer for Google Cloud, said that the attack occurred in September 2017 and used 180,000 exposed CLDAP, DNS, and SMTP servers to amplify responses directed at Google.
The effort, large as it was, did not create problems and Google services and infrastructure remained unscathed.
“Despite simultaneously targeting thousands of our IPs, presumably in hopes of slipping past automated defenses, the attack had no impact” – Damian Menscher
Menscher says that the size of the attack, which is the largest ever disclosed publicly, shows “the volumes a well-resourced attacker can achieve,” noting that it was four times larger than the Mirai DDoS attack that shook the internet in 2016.
Another large attack was recorded this year from an IoT botnet. It targeted the network protocol and hit with 690 million packets per second (mpps)
In a report at the beginning of the year, Amazon AWS reported a 2.3Tb per second volumetric DDoS attack, recorded in the first quarter of 2020.
The largest packet rate per second mitigated by Amazon in that period was 293.1 Mpps, more than two times smaller than the one Google recorded this year.
Google warns that while its report shows the scale of past and current DDoS attacks and can help predict the size of future ones, defenses must be over-provisioned so they can withstand attacks of unexpected sizes.
Collaborating with partners in the internet community (network providers, vendors, customers) can help mitigate large attacks in a timely manner. Network providers can trace bad packets and filter them, vendors can provide patches and alert customers to apply them.
As the internet keeps growing, it provides resources to both adversaries and defenders. Knowing what to expect, defenders can determine the capacity they need to resist the largest attacks.
To read the original article :



