ThunderX has changed its name to Ranzy Locker and launched a data leak site where they shame victims who do not pay the ransom.
ThunderX is a ransomware operation that was launched at the end of August 2020. Soon after launching, weaknesses were found in the ransomware that allowed a free decryptor to be released by Tesorion.
The ransomware operators quickly fixed their bugs and released a new version of the ransomware under Ranzy Locker name.
While the name has changed, strings associated with a PDB debug file in the ransomware executables still show it is the same as ThunderX.
C:\Users\Gh0St\Desktop\ThunderX\Release\LockerStub.pdbBleepingComputer’s theory is that they rebranded to start with a clean slate and avoid the stigma of being associated with the previously released decryptor.
Meet the Ranzy Locker ransomware
Using a sample of the ransomware found by MalwareHunterteam and shared with BleepingComputer, we can get a deeper dive into how the ransomware operates.
When launched, Ranzy Locker will first clear Shadow Volume Copies so that victims can’t use it to recover encrypted files.
vssadmin.exe Delete Shadows /All /Quiet;When encrypting files, the ransomware will use a Windows API called the ‘Windows Restart Manager’ that will terminate processes or Windows services that keep a file open and prevent it from being encrypted.
For each encrypted file, the ransomware appends the new .ranzy extension to the file’s name. For example, a file named 1.doc would be encrypted and renamed to 1.doc.ranzy.
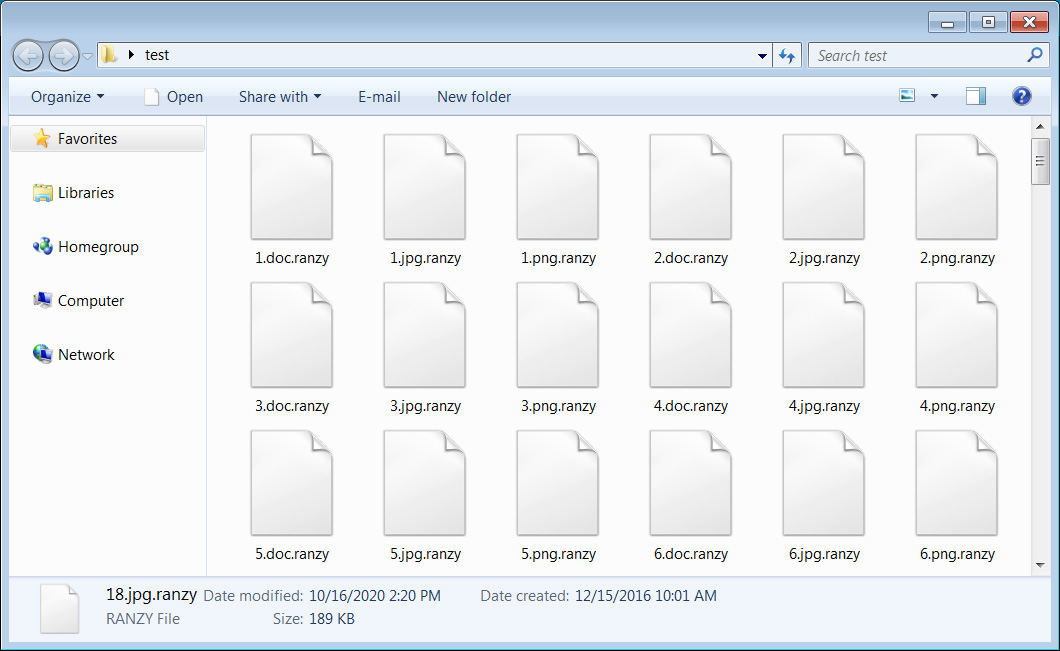
In each traversed folder, the ransomware will create a ransom note named ‘readme.txt‘ that includes information about what happened to a victim’s data, a warning that their data was stolen, and a link to a Tor site where the victim can negotiate with the threat actors.
It should be noted that in previous versions of ThunderX, the ransomware operators communicated with victims via email rather than using a dedicated Tor site.
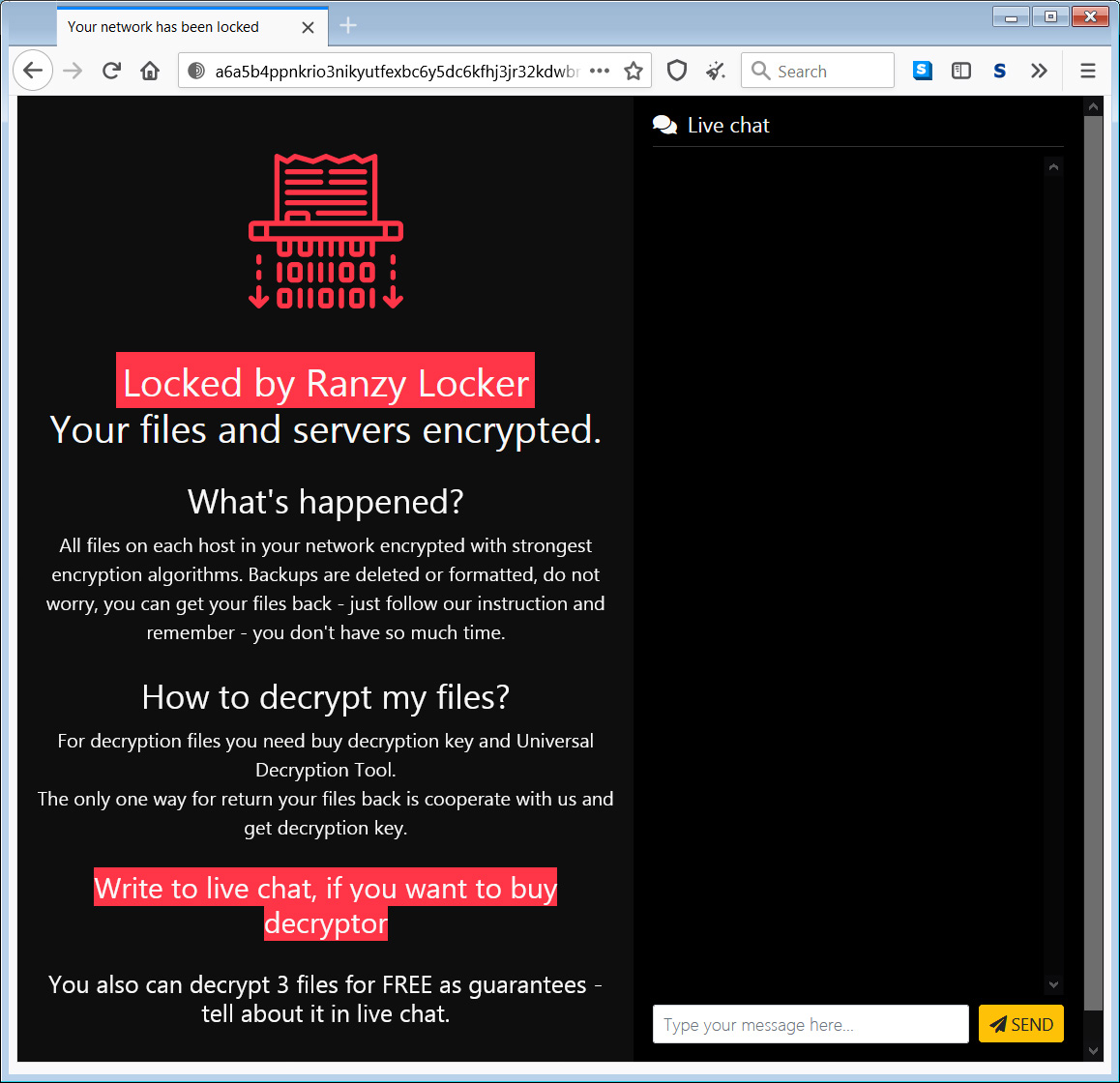
When a victim visits the Tor payment site, they will be greeted with a ‘Locked by Ranzy Locker’ message and be shown a live chat screen to negotiate with the threat actors. As part of this ‘service,’ the ransomware operators allow victims to decrypt three files for free to prove that they can do so.
Ranzy Locker launches a data leak site
Many ransomware gangs utilize a double-extortion attack method, which is to steal unencrypted files from a victim before they encrypt the devices on the corporate network.
This attack method provides the threat actors two ways to leverage the victim into paying a ransomware — pay to get their files back and not have their data publicly leaked.
This week, the Ranzy Locker gang released a data leak site called ‘Ranzy Leak’ to leak the data of victims who do not pay.
This web site currently includes one victim who develops power control solutions.
An item of interest is that the Tor onion URL used by the Ranzy Leak site is the same as the one previously used by Ako Ransomware.
The use of Ako’s URL could indicate that both groups merged to form Ranzy Locker, or they are cooperating similarly as the Maze cartel.
Update 10/16/20: The Ako ransomware operators contacted us and stated ThunderX is part of their operation and that they have rebranded to Ranzy Locker.
“Because we update our original ransomware and its little rebranding.
ThunderX is test version our update, but some US kids share this build on virustotal — oops.
To read the original article:



