A malware campaign ongoing since the beginning of the year has recently changed tactics, switching from exploit kits to social engineering to target adult content consumers.
The operators use an old trick to distribute a variant of ZLoader, a banking trojan that made a comeback earlier this year after an absence of almost two years, now used as an info stealer.
Named Malsmoke by security researchers, the campaign focuses on high-traffic adult portals. Some websites, like xHamster, rake hundreds of millions of monthly visitors. Another site is Bravo Porn Tube, with over 8 million visitors every month.
Malwarebytes monitored the Malsmoke campaign all year long delivering Smoke Loader – a malware dropper – via Fallout exploit kit until its track went cold on October 18.
The operators had not given up, though. They had switched to a new technique that works on all web browsers: a new malicious campaign that uses “a decoy page filled with adult images purporting to be movies.”
Using a fake video on an adult website, they lured visitors into playing it. The deceptive file would open in a new browser window and instead of images, victims would get a pixelated view and a few seconds of audio to keep them enticed.
After a few seconds, victims would see an overlay message telling them that Java Plug-in needs to be installed for the video to play correctly.

This is an old trick that hails back from the time when it was common for media data streams to be encoded with various codecs (compression-decompression software). A such, media could not be played without the correct codec installed.
Back then, a plethora of fake codecs and media players existed, many of them malicious. Adware and malware would be distributed using this method.
Malsmoke operators created the grainy videos specifically, to make it look like some piece of software is missing. However, Malwarebytes researcher note in their report that showing a Java update as a solution for video streaming issues is a strange choice since it’s typically used for other tasks.
“The threat actors could have designed this fake plugin update in any shape or form. The choice of Java is a bit odd, though, considering it is not typically associated with video streaming. However, those who click and download the so-called update may not be aware of that, and that’s really all that matters” – Malwarebytes
The researchers linked the old Malsmoke campaigns with the new one after analyzing the network indicators and noticing that the same templates for the decoy websites were used in both cases.
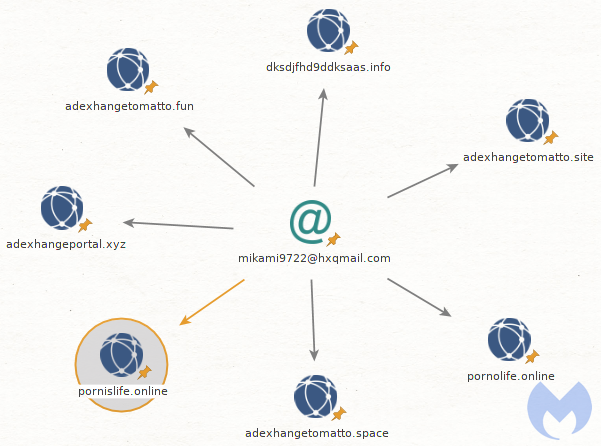
Furthermore, the cybercriminals used an email address to register a new domain for the new campaign that was already associated with other domains used in previous operations.
When analyzing the payload, the researcher found that the fake Java update is a signed installer that contains mostly legitimate libraries and executable files.
One of them – HelperDll.dll – downloaded an encrypted variant of ZLoader (also known as Zbot, Zeus Sphinx, Terdot, and DELoader) and deployed it as the final payload.
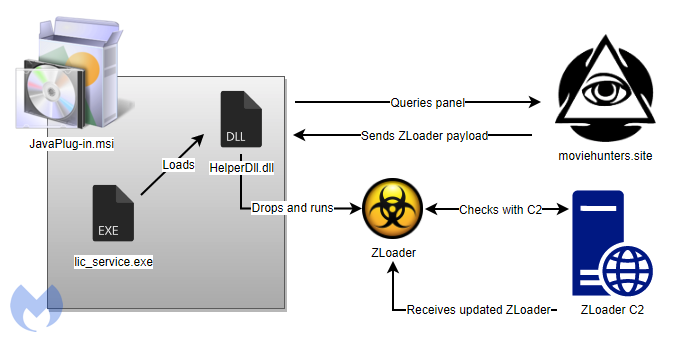
The malware went silent in early 2018 but resurged in more than 100 email campaigns in six months since December 2019. It is likely a fork of the original threat that lacks some advanced features.
The current variant of ZLoader preserved the main functions and uses web injects to steal credentials, banking information, and sensitive details stored in browsers (cookies, passwords).
By switching to this tactic, Malsmoke operators have widened their reach to an audience of millions of potential victims. This change is a huge jump considering that successful compromise via exploit kits requires the all-but-buried Internet Explorer.
Malwarebytes provides a list of indicators of compromise for the adult sites used in this campaign as well as for the decoys and command and control centers.
To read the original article:



