The U.S. Federal Bureau of Investigation (FBI) Cyber Division has warned private industry partners of increased Ragnar Locker ransomware activity following a confirmed attack from April 2020.
The MU-000140-MW flash alert issued to partners by the FBI yesterday was coordinated with DHS-CISA and it provides security professionals and system admins with indicators of compromise to guard against the persistent malicious actions of this ransomware gang.
“The FBI first observed Ragnar Locker1ransomwarein April 2020, when unknown actors used it to encrypt a large corporation’s files for an approximately $11 million ransom and threatened to release 10 TB of sensitive company data,” the FBI says in the TLP:WHITE flash alert.
“Since then, Ragnar Locker has been deployed against an increasing list of victims, including cloud service providers, communication, construction, travel, and enterprise software companies.”
Ragnar Locker tactics
Ragnar Locker actors will manually deploy the ransomware payloads to encrypted the victims’ systems after a reconnaissance stage to help them discover network resources, company backups, and various other sensitive files to be collected for data exfiltration.
The ransomware gang is also known for frequently switching payload obfuscation techniques to evade detection, as well as for having used custom packing algorithms and encrypting the victims’ files from Windows XP virtual machines deployed on their systems.
Ragnar Locker’s malware will also list all running services to kill those used by managed service providers to remotely manage their clients’ networks.
After going through reconnaissance and pre-deployment stages, Ragnar Locker actors drop a highly targeted ransomware executable that adds a custom “RGNR_” extension where is a hash of the computer’s NETBIOS name.
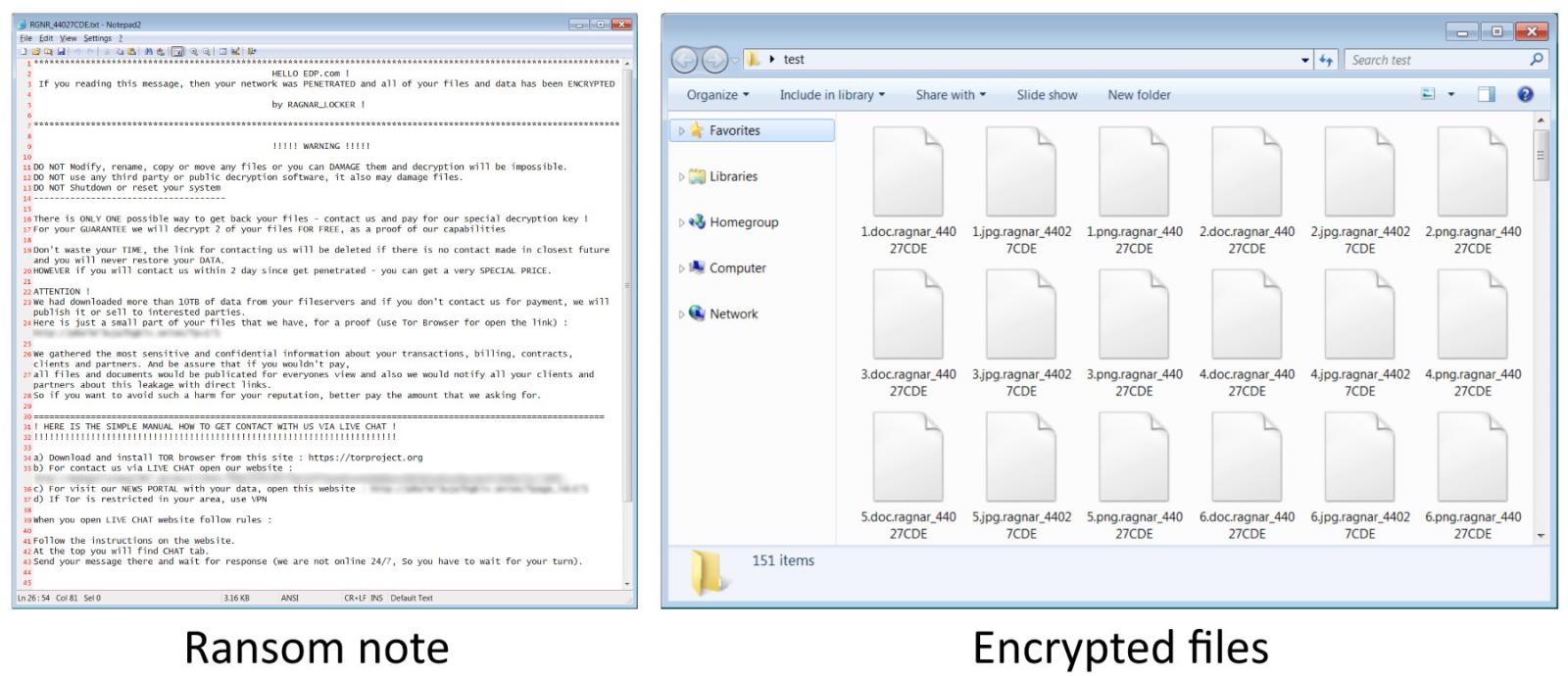
This ransomware features an embedded RSA-2048 key and it will also drop custom ransom notes on encrypted systems.
The Ragnar Locker ransom notes include the victim’s company name, a link to the Tor site, and the data leak site where the ransomware gang will publish the victim’s data.
EDP ransomware attack
While the FBI did not provide further info regarding the large corporation whose systems were encrypted in April, the details perfectly match an attack against the multinational energy giant Energias de Portugal (EDP).
EDP is one of the largest European energy sector operators with over 11.500 employees and it delivers energy to more than 11 million customers in 19 countries and on 4 continents.
The Ragnar Locker attackers were able to exfiltrate roughly 10TB of confidential company information on billing, contracts, transactions, clients, and partners.
They also stole a KeePass password manager database export containing EDP employees’ login names, passwords, accounts, URLs, and notes.
An EDP spokesperson told BleepingComputer that the attack had no impact on the company’s critical infrastructure and power supply service.
During the last year, the FBI has also issued warnings on LockerGoga, MegaCortex, Maze, Netwalker, and ProLock ransomware following a public service announcement regarding high-impact ransomware attacks against public and private U.S. organizations from October 2019.
To read the original article:



