After a year-long vacation, the Gootkit information-stealing Trojan has returned to life alongside REvil Ransomware in a new campaign targeting Germany.
The Gootkit Trojan is Javascript-based malware that performs various malicious activities, including remote access for threat actors, keystroke capturing, video recording, email theft, password theft, and the ability to inject malicious scripts to steal online banking credentials.
Last year, the Gootkit threat actors suffered a data leak after leaving a MongoDB database exposed on the Internet. After this breach, it was believed that the Gootkit actors had shut down their operation until they suddenly came alive again earlier this month.
Gootkit bursts back to life with ransomware partnership
Last week, a security researcher known as The Analyst told BleepingComputer that the Gootkit malware had emerged again in attacks targeting Germany.
In this new malicious campaign, threat actors are hacking WordPress sites and utilizing SEO poisoning to display fake forum posts to visitors. These posts pretend to be a question and answers with a link to fake forms or downloads.
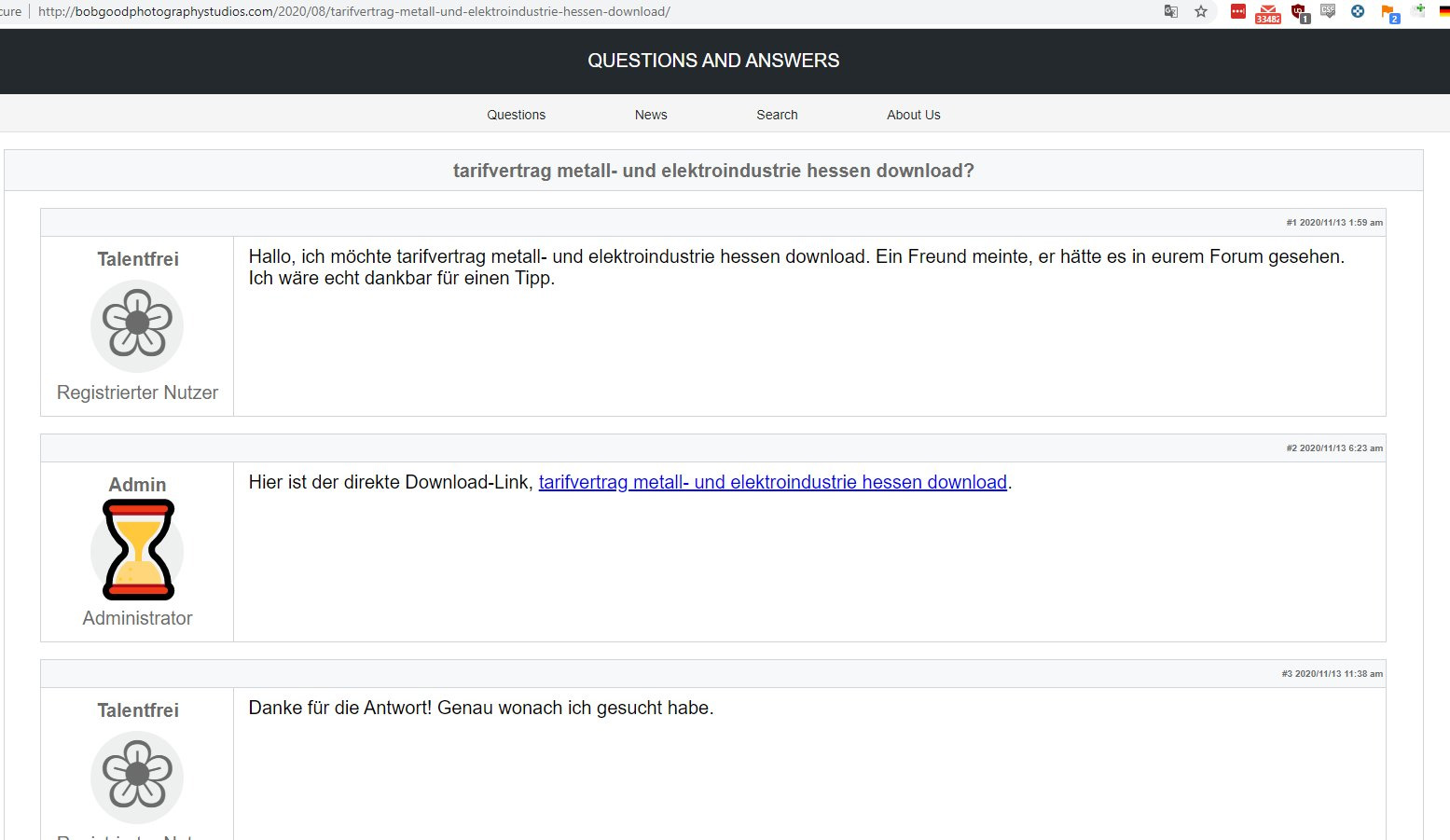
When the user clicks on the link, they will download a ZIP file containing an obfuscated JS file that will install either the Gootkit malware or the REvil ransomware.
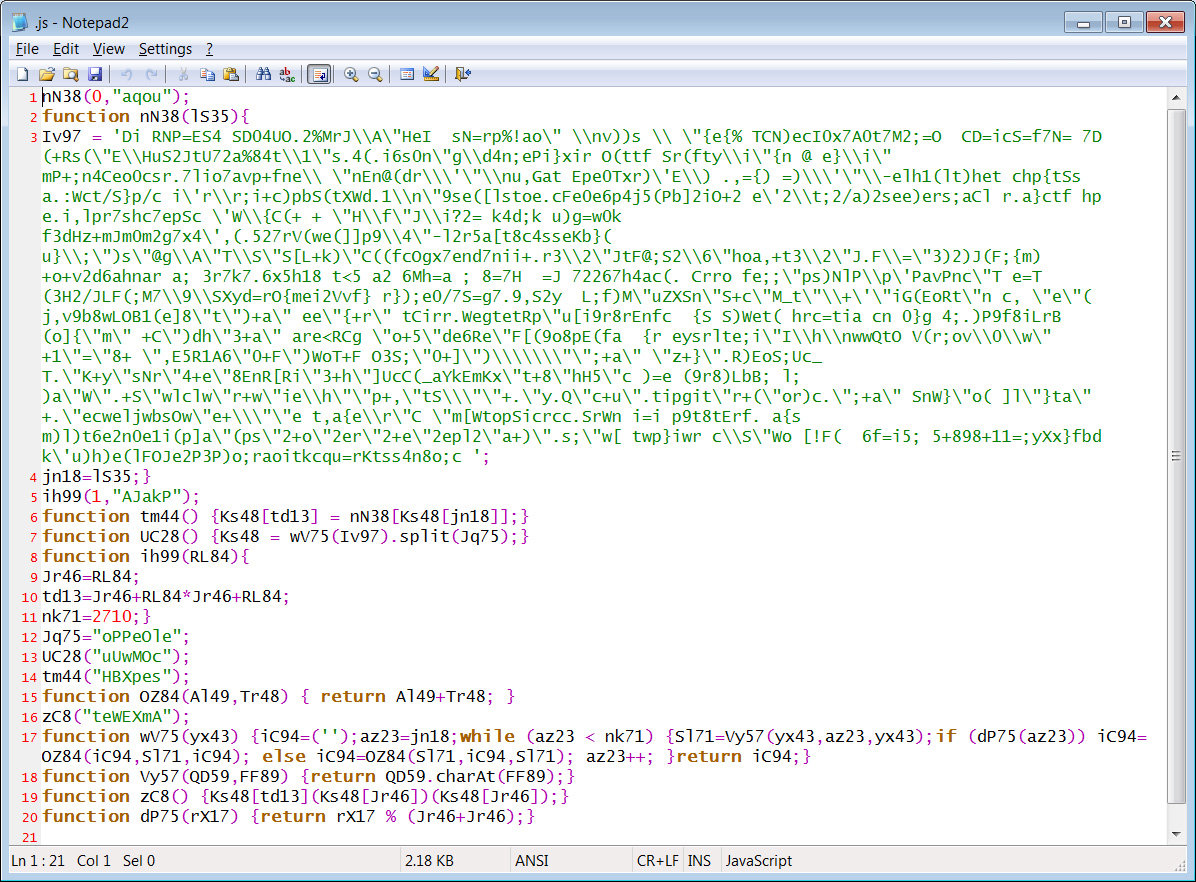
This same distribution method was previously used by REvil in September 2019, around the same time that Gootkit had disappeared.
Gootkit and REvil installed in fileless attacks
In a new report released today, Malwarebytes’ researchers explain that the malicious JavaScript payloads will perform fileless attacks of either Gootkit or REvil.
When launched, the JavaScript script will connect to its command and control server and downloads another script that contains the malicious malware payload.
In Malwarebytes’ analysis, this payload is usually Gootkit, but it was also REvil ransomware in some cases.
“After conversion to ASCII, the next JavaScript is revealed, and the code is executed. This JavaScript comes with an embedded PE payload which may be either a loader for Gootkit, or for the REvil ransomware. There are also some differences in the algorithm used to deobfuscate it,” Malwarebytes stated in their report.
These payloads would be stored as Base64 encoded or hexadecimal strings in either a text file or split up into numerous Windows Registry values, as shown below.
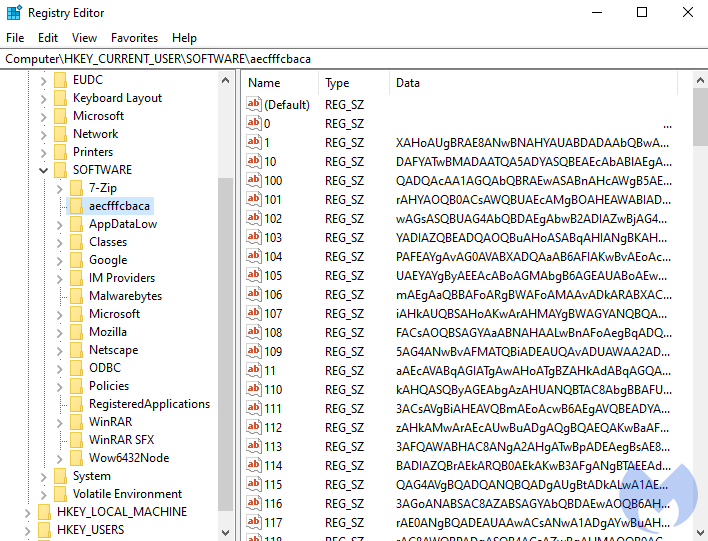
Source: Malwarebytes
The loader will eventually read the Registry or text file’s payloads, decode it, and filelessly launch the process directly into memory.
Using obfuscated payloads and to break them up into pieces stored in the Registry, makes it harder for security software to detect the malicious payloads.
“The threat actors behind this campaign are using a very clever loader that performs a number of steps to evade detection. Given that the payload is stored within the registry under a randomly-named key, many security products will not be able to detect and remove it,” Malwarebytes explains.
An interesting discovery found by The Analyst when testing this malicious campaign was that the Revil infection dropped ransom notes used in previous attacks.
This error was likely caused by the distribution campaign using an older version of REvil ransomware and forgetting to refresh it with a newer version.



