A severe authentication bypass vulnerability has been reported in Bouncy Castle, a popular open-source cryptography library.
When exploited, the vulnerability (CVE-2020-28052) can allow an attacker to gain access to user or administrator accounts due to a cryptographic weakness in the way passwords are checked.
Bouncy Castle is a set of cryptography APIs used by both Java and C#/.NET developers building security applications who’d rather not worry about rolling their own cryptographic algorithms.
The .NET version of Bouncy Castle alone has been downloaded over 16,000,000 times, speaking to the seriousness of vulnerabilities in Bouncy Castle, a library relied on by developers of mission-critical applications.
Flawed password hashing algorithm
This week, two researchers Matti Varanka and Tero Rontti from Synopsys Cybersecurity Research Center have disclosed an authentication bypass vulnerability in Bouncy Castle.
The flaw, tracked as CVE-2020-28052, exists in the OpenBSDBcrypt class of Bouncy Castle which implements the Bcrypt password hashing algorithm.
That is, the Bcrypt.doCheckPassword() function responsible for performing a byte-by-byte password hash match has an erroneous logic in place.
“The code checks for an index of characters from 0 to 59 inclusive, rather than checking that characters at positions from 0 to 59 match,” reads the report published by Synopsys.
“This means that passwords that result in hashes that, for instance, don’t contain bytes between 0x00 and 0x3B match every other password hash that don’t contain them. Passing this check means an attacker doesn’t need a byte-for-byte match with the stored hash value,” continues the report.
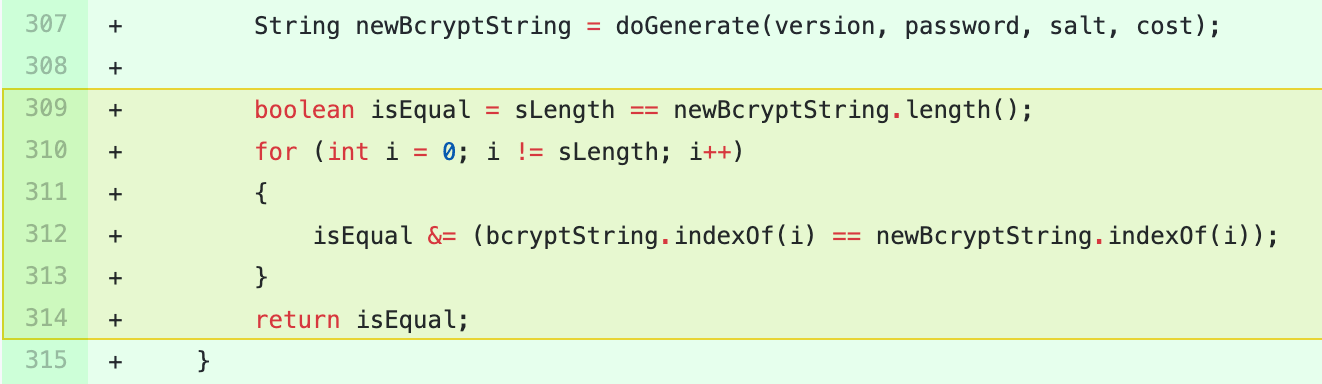
What this essentially comes down to is, brute-forcing a set of strings that will yield a hash which, when compared by the doCheckPassword() function returns true (i.e. match successful).
Successful exploitation of the flaw means, an attacker could brute-force the password for any user account, including the administrator’s, should an application’s hash-based password checks be using Bouncy Castle.
High success rate on first 1,000 attempts
While strong passwords take a very long time to crack via brute-forcing, this implementation flaw “short circuits” the verification routine, letting this assumption slip.
On average, the researchers observed that 20% of tested passwords could be brute-forced on the first thousand attempts as a result of exploiting this vulnerability.
“Some password hashes take more attempts, determined by how many bytes lie between 0 and 60 (1 to 59). Further, our investigation shows that all password hashes can be bypassed with enough attempts. In rare cases, some password hashes can be bypassed with any input,” stated the report.
Bcrypt hashing-based authentication, according to the researchers, is used for authentication checks in web applications and APIs.
Given that, the vulnerability has been assigned a High severity CVSS 3.1 rating.
According to the researchers, both Bouncy Castle 1.65 and 1.66 are impacted by this flaw but not versions prior to 1.65.
Bouncy Castle has applied a fix for this vulnerability in versions 1.67 and above and developers are encouraged to apply the upgrade.
To read the original article:



