Almost a dozen Dell Wyse thin client models are vulnerable to critical issues that could be exploited by a remote attacker to run malicious code and gain access to arbitrary files.
Thin clients are small form-factor computers used for remote desktop connections to a more powerful system. They are popular with organizations that don’t need computers with high processing, storage, and memory on the network.
It is estimated that more than 6,000 organizations, most of them from the healthcare sector, have deployed Dell Wyse thin clients on their networks.
Configuration file at risk
The vulnerabilities (tracked as CVE-2020-29492 and CVE-2020-29491) are in components of ThinOS, the operating system on Dell Wyse thin clients.
ThinOS can be maintained remotely. Dell’s recommendation for this procedure is to set up an FTP server for devices to download updates (firmware, packages, configurations).
Security researchers at CyberMDX, a company focusing on cybersecurity in the healthcare sector, found that FTP access is possible with no credentials, using “anonymous” user.
They also discovered that only the firmware and packages are signed, leaving INI configuration files as a possible way for a malicious actor to do some damage.
Elad Luz head of research at CyberMDX, says that there is also a specific INI file on the FTP server that should be writeable for the connecting clients.
“Since there are no credentials, essentially anyone on the network can access the FTP server and modify that INI file holding configuration for the thin client devices”- Elad Luz
Protecting the FTP connection with credentials would not be enough under the current design, says Luz, because the username and password would be shared across the entire fleet of thin clients.
The researcher explains that when a Dell Wyse device connects to the FTP server, it looks for the INI file that holds its configuration, named after the username used in the terminal.
With this file being writeable, an attacker can plant a malicious version to control the configuration received by a specific user on the network.
One scenario an attacker could leverage these vulnerabilities is to read or modify parameters in the configuration file that would give them remote control over the thin device. Leaking credentials or manipulating DNS results are also on the list of risks that could stem from exploiting the two bugs.
Not all models
According to CyberMDX, these vulnerabilities affect the following Dell Wyse models running ThinOS 8.6 and below:
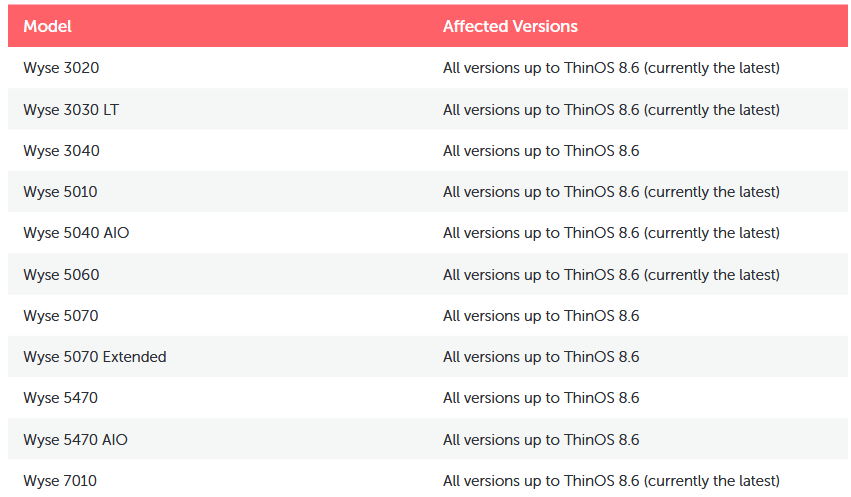
Dell has released ThinOS 9.x to address these issues. However, some of the affected models can no longer be upgraded:
- Wyse 3020
- Wyse 3030 LT
- Wyse 5010
- Wyse 5040 AIO
- Wyse 5060
- Wyse 7010
CyberMDX recommends that organizations with the models above deployed on their networks disabled the use of FTP for the update procedure and rely on an alternative method for the task.
In its security advisory, Dell recommends securing the environment by using a secure protocol (HTTPS) and ensuring that the file servers have read-only access.
Additionally, impacted customers can use Wyse Management Suite for imaging and device configuration, which enforces the use of HTTPS and stores the configuration files in a secure server database.
To read the original article:



