Overview
This is my report for the new Babuk Ransomware that recently appears at the beginning of 2021.
Since this is the first detection of this malware in the wild, it’s not surprising that Babuk is not obsfuscated at all. Overall, it’s a pretty standard ransomware that utilizes some of the new techniques we see such as multi-threading encryption as well as abusing the Windows Restart Manager similar to Conti and REvil.
For encrypting scheme, Babuk uses its own implementation of SHA256 hashing, ChaCha8 encryption, and Elliptic-curve Diffie–Hellman (ECDH) key generation and exchange algorithm to protect its keys and encrypt files. Like many ransomware that came before, it also has the ability to spread its encryption through enumerating the available network resources.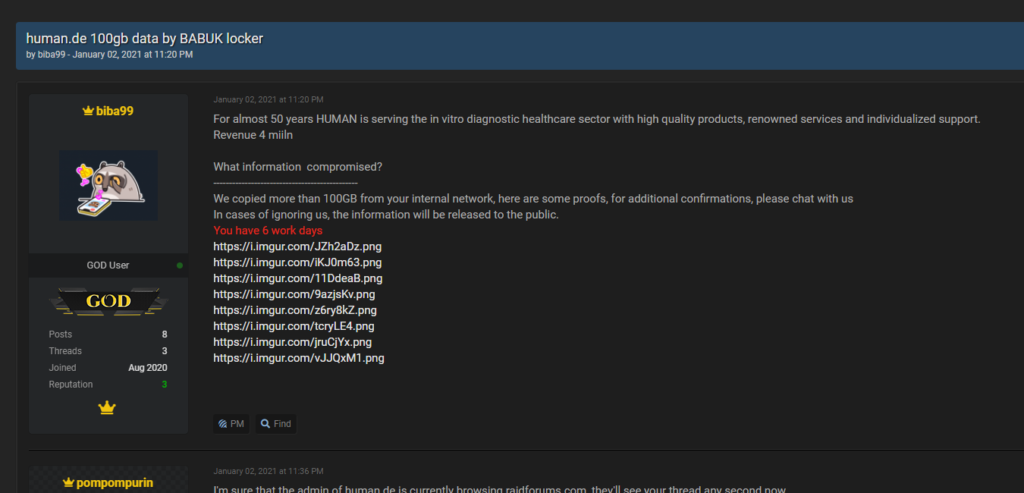
Figure 1: RaidForum Babuk leak
IOCS
Babuk Ransomwarecomes in the form of a 32-bit .exe file.
MD5: e10713a4a5f635767dcd54d609bed977
SHA256: 8203c2f00ecd3ae960cb3247a7d7bfb35e55c38939607c85dbdb5c92f0495fa9
Sample: https://bazaar.abuse.ch/sample/8203c2f00ecd3ae960cb3247a7d7bfb35e55c38939607c85dbdb5c92f0495fa9/
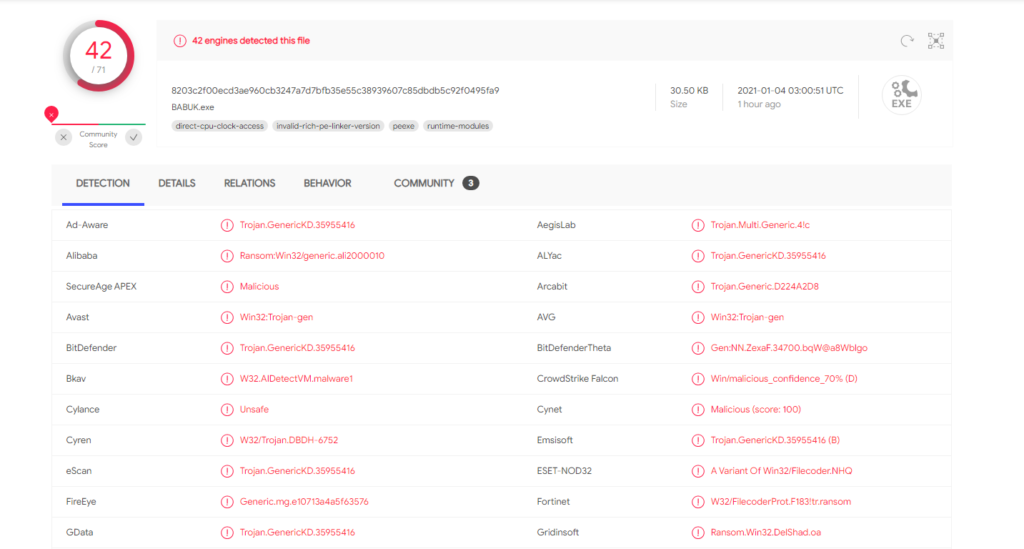
Figure 2: VirusTotal result
Ransom Note
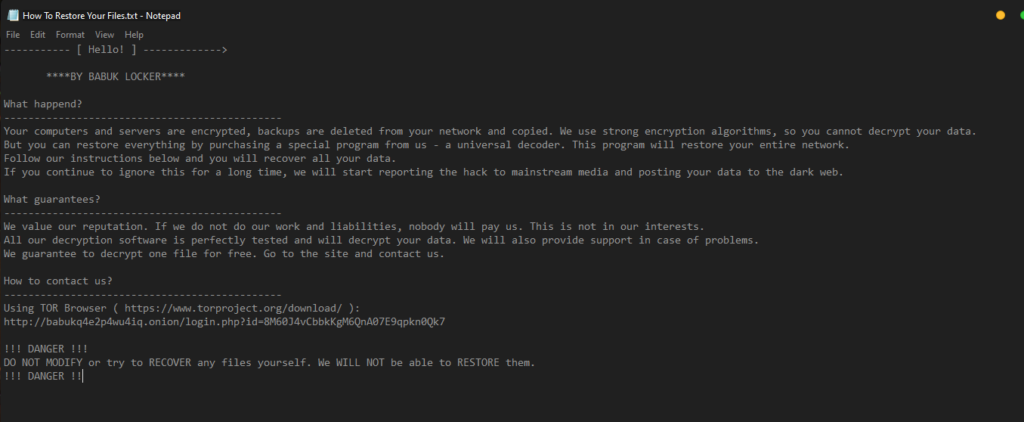
Figure 3: Babuk’s ransom note
To read the original article:
http://chuongdong.com/reverse%20engineering/2021/01/03/BabukRansomware/



