As sophisticated attacks dominate the headlines, it’s important to remember that the vast majority of cybercrime results from simple, effective, and tested tools. These tools are easy to use and accommodate a wide range of attacker skill levels. The LogoKit phishing kit, which RiskIQ has detected running on more than 300 unique domains in the past week and 700 over the past month, is a prime example.
Simple deception is still useful for picking off large groups of victims, and operators of LogoKit know this all too well. Unlike many other phishing kits, the LogoKit family is an embeddable set of JavaScript functions designed to interact within the Document Object Model (DOM), the site’s presentation layer. Integrating with the DOM allows for the script to dynamically alter the visible content and HTML form data within a page, all without user interaction. This capability gives attackers a wide range of options for visually deceiving their victims by easily integrating it into existing HTML pretext templates or building fake forms to mimic corporate login portals.
LogoKit is More than Meets the Eye
LogoKit operators send victims a personalized, specially crafted URL containing their email address. Once a victim navigates to the URL, LogoKit fetches the desired company logo from a third-party service, such as Clearbit or Google’s favicon database. The victim email is also auto-filled into the email or username field, tricking victims into thinking it’s a familiar site they’ve already visited and logged into. In some cases, attackers use legitimate object storage buckets, i.e., Google Firebase, which helps their operation appear less suspicious because it sends users to a domain name they recognize.
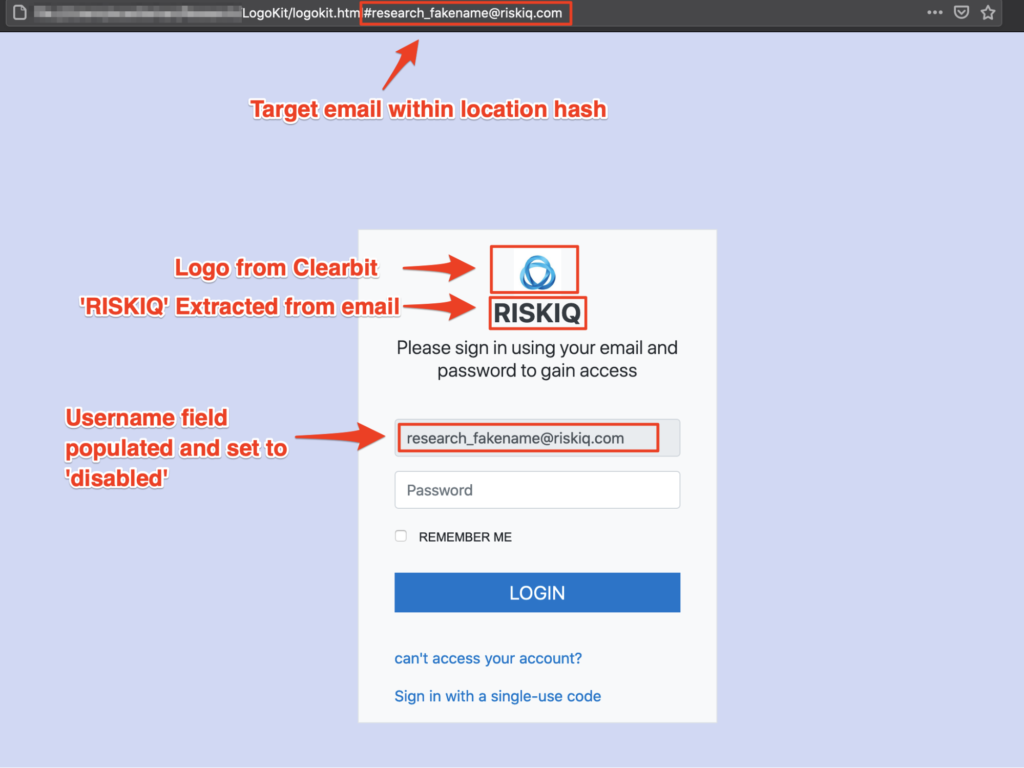
How LogoKit works
Should a victim enter their password, LogoKit performs an AJAX request sending their email and password to an attacker-owned server before finally redirecting the user to the corporate website they intended to visit when clicking the URL. However, some LogoKit versions will play additional tricks, such as telling a user that their password is incorrect and prompting them to enter the password again. Another AJAX request can then perform new tasks, such as sending the credentials to the attacker’s email.
For Phishing, Simpler is Better
LogoKit is ingenious in its simplicity. It’s fully modularized, allowing for effortless reuse and adaptation by other threat actors without the need for changing templates. The LogoKit script itself even makes it easy for attackers to compromise websites to embed malicious scripts or host attacker infrastructure—RiskIQ has observed websites hosting LogoKit variants via compromised WordPress instances.
LogoKit is also powerful in its versatility. It can be used in simple login forms or embedded into more complex HTML documents pretending to be legitimate services. This ability to disguise as or blend into almost any site makes it popular with attackers who have targeted a wide range of victims. RiskIQ has observed LogoKit mimicking organizations across several sectors, including financial, legal, and entertainment.
RiskIQ has observed LogoKit operators targeting various services, ranging from generic login portals to SharePoint, Adobe Document Cloud, OneDrive, Office 365, and Cryptocurrency exchanges. In using only widely used services, threat actors ensure blocking LogoKit will be tricky. For example, blocking Amazon’s object storage outright would likely lead to availability issues for legitimate web browsing.
Other services targeted by LogoKit observed by RiskIQ include:
- glitch.me: Application Deployment Platform
- appspot.com: Google Cloud Platform
- web.app: Google Firebase
- firebaseapp.com: Google Firebase
- storage.googleapis.com: Google Cloud Storage
- firebasestorage.googleapis.com: Google Firebase Storage
- s3.amazonaws.com: Amazon S3 Object Storage
- csb.app: Google CodeSandbox
- website.yandexcloud.net: Yandex Static Hosting
- github.io: GitHub Static Page Hosting
- digitaloceanspaces.com: DigitalOcean Object Storage
- oraclecloud.com: Oracle Object Storage
Vigilance is Key Against LogoKit
As mentioned above, many attacks using LogoKit involved preformatted URLs sent to victims, which emphasizes the importance of security awareness and phishing training for users. The following redacted URL serves as an example LogoKit phish link observed within RiskIQ’s data:
hxxps://324634XXXa2616-dot-XXXX 301XX4.df.r.appspot.com/#recruitmentXXX@XXX.com
Because threat actors can easily embed LogoKit payloads inside legitimate pages or create subdirectories for LogoKit deployment, site administrators should regularly review their CMS for updates. They should also be on top of web applications’ login pages’ integrity by looking for injected code.
Detecting LogoKit
LogoKit continues the trend of threat actors using simple tools that leave small digital footprints. In executing only a few lines of customizable JavaScript and loading resources from trusted sources, LogoKit operators have a high rate of success. With the flexibility of having numerous delivery methods—compromised infrastructure, attacker-hosted infrastructure, and object storage—attackers can quickly change their delivery source.
RiskIQ’sInternet Intelligence Graph gives security teams a universal view of the internet and is now detecting LogoKit code on a global scale. It also gives our customers a full-stack view of their organization’s attack surface, including changes to JavaScript that may indicate LogoKit code’s presence. RiskIQ’s crawls of our customers’ web properties give them insight into what’s happening on a web server at any given time and how that server would interact with a real user.
To read the original article:
https://www.riskiq.com/blog/external-threat-management/logokit-phishing/



