The Babyk ransomware operation has launched a new data leak site used to publish victim’s stolen data as part of a double extortion strategy. Included is a list of targets they wont attack with some exclusions that definitely stand out.
In 2019, the Maze ransomware operation introduced a new double-extortion strategy of stealing unencrypted files and then threatening to publicly release them on data leak sites if a ransom is not paid.
Soon after, other ransomware gangs adopted this strategy until it has become a popular method for threat actors to extort their victims.
Babyk launches a data leak site
Babyk ransomware, also known as Babuk, is a new ransomware operation that launched at the beginning of the year and has been targeting enterprise organizations worlwide.
When first launched, the ransomware gang was leaking their data in posts on the ‘Raid Forums’ hacking forum but had stated that they planned on launching a dedicated leak site.
Emsisoft security researcher Brett Callow shared a new site recently created by the Babyk Ransomware group where they are currently listing four victims, and the leaked data for three of them.
Included on the data leak site is a list of organizations that they will not encrypt, which includes hospitals, non-profits, schools, and small businesses.
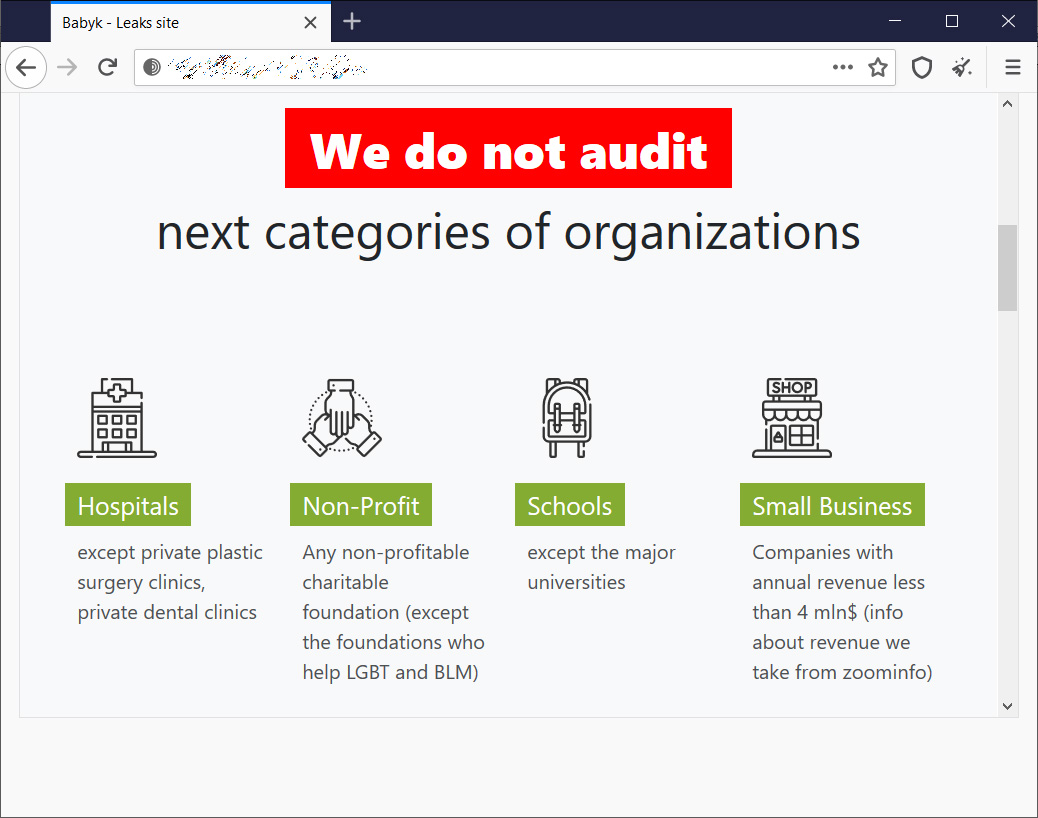
For each of these categories, the ransomware gangs lists the following exclusions:
We do not audit next categories of organizationsHospitals: except private plastic surgery clinics, private dental clinics
Non-Profit: Any non-profitable charitable foundation (except the foundations who help LGBT and BLM)
Schools: except the major universities
Small Business: Companies with annual revenue less than 4 mln$ (info about revenue we take from zoominfo)
BleepingComputer has seen exclusion in the past for healthcare and what ransomware actors call “socially vital” services, such as 911, shelters, and nursing homes.
The exclusions for non-profits is the first time BleepingComputer has seen personal opinions dictate whether a ransomware operation will encrypt an organization.
With the release of Babuk’s site, there are now a total of ninteeen active ransomware data leak sites used in the double extortion tactic.
To read the original article:



