Days after the first malware targeting Apple M1 chips was discovered in the wild, researchers have disclosed yet another previously undetected piece of malicious software that was found in about 30,000 Macs running Intel x86_64 and the iPhone maker’s M1 processors.
However, the ultimate goal of the operation remains something of a conundrum, what with the lack of a next-stage or final payload leaving researchers unsure of its distribution timeline and whether the threat is just under active development.
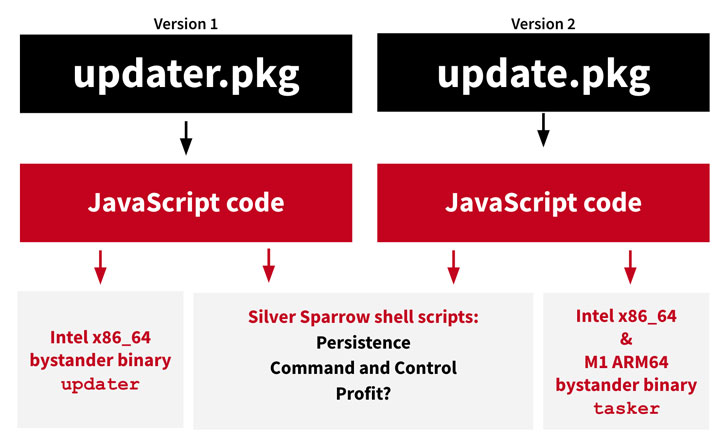
Calling the malware “Silver Sparrow,” cybersecurity firm Red Canary said it identified two different versions of the malware — one compiled only for Intel x86_64 and uploaded to VirusTotal on August 31, 2020 (version 1), and a second variant submitted to the database on January 22 that’s compatible with both Intel x86_64 and M1 ARM64 architectures (version 2).
Adding to the mystery, the x86_64 binary, upon execution, simply displays the message “Hello, World!” whereas the M1 binary reads “You did it!,” which the researchers suspect is being used as a placeholder.
“The Mach-O compiled binaries don’t seem to do all that much […] and so we’ve been calling them ‘bystander binaries,'” Red Canary’s Tony Lambert said.
“We have no way of knowing with certainty what payload would be distributed by the malware, if a payload has already been delivered and removed, or if the adversary has a future timeline for distribution,” Lambert added.
The 29,139 macOS endpoints are located across 153 countries as of February 17, including high volumes of detection in the U.S., the U.K., Canada, France, and Germany, according to data from Malwarebytes.
Despite the difference in the targeted macOS platform, the two samples follow the same modus operandi: using the macOS Installer JavaScript API to execute attack commands by dynamically generating two shell scripts that are written to the target’s file system.
While “agent.sh” executes immediately at the end of the installation to inform an AWS command-and-control (C2) server of a successful installation, “verx.sh” runs once every hour, contacting the C2 server for additional content to download and execute.
Additionally, the malware also comes with the capabilities to completely erase its presence from the compromised host, suggesting the actors associated with the campaign may be motivated by stealth techniques.
In response to the findings, Apple has revoked the binaries that were signed with the Apple Developer ID’s Saotia Seay (v1) and Julie Willey (v2), thus preventing further installations.
Silver Sparrow is the second piece of malware to contain code that runs natively on Apple’s new M1 chip. A Safari adware extension called GoSearch22 was identified last week to have been ported to run on the latest generation of Macs powered by the new processors.
“Though we haven’t observed Silver Sparrow delivering additional malicious payloads yet, its forward-looking M1 chip compatibility, global reach, relatively high infection rate, and operational maturity suggest Silver Sparrow is a reasonably serious threat, uniquely positioned to deliver a potentially impactful payload at a moment’s notice,” Lambert said.
To read the original article:https://thehackernews.com/2021/02/new-silver-sparrow-malware-infected.html?