ATMs across Latin America have been persistently targeted over the last eight years by organized criminals seeking to “jackpot” the machines, triggering them to disgorge their cash.
The attacks typically involve installing malware directly on an ATM by breaking into the device’s cabinet to gain direct access to its physical ports and drives. In the early days, around 2013, this involved using a CD boot disk to install the malware, dubbed “Ploutus.”
Now, researchers with Mexico-based Metabase Q, a cybersecurity services company, have uncovered a new version called Ploutus-I. This fifth known iteration of Ploutus was first seen in Mexico. Metabase Q strongly suspects its development has been closely connected with organized criminals, perhaps based in Venezuela.
Ploutus-I targets aging ATM models made by Itautec, which at one time was the second-largest manufacturer of ATMs in Brazil. In 2014, Itautec’s ATM business was acquired by a Japanese company, OKI, short for OKI Electric Industry. About two years ago, NCR bought most of OKI’s IT services operations in Brazil.
Metabase Q CEO and founder Mauricio Benavides says the company’s analysts examined samples of Ploutus-I in addition to a physical ATM that had been infected. “We’ve been seeing it in the market in different places, so it’s not particular to one [bank],” Benavides says.
Ploutus: Clever Engineering
Ploutus is a clever piece of malicious malware engineering. It’s a bespoke program that is the result of an intensive study of an ATM’s software stack, Metabase Q says.
ATMs typically run a version of Microsoft Windows. But Windows was never designed to run ATMs, so most run Extensions for Financial Services or XFS, which is a set of APIs designed to link the host Windows systems to the specific features of ATMs, such as displays and PIN pads.
ATM vendors usually use a layer of middleware to interact with XFS. NCR’s version is called Aptra. Diebold Nixdorf’s version is called Agilis. A Munich-based company called KAL makes Kalignite, which is compatible with many ATM vendors and makes cross-compatibility easier for banks.
Previous versions of Ploutus targeted specific versions of middleware, as seen in the graph from Metabase Q below.
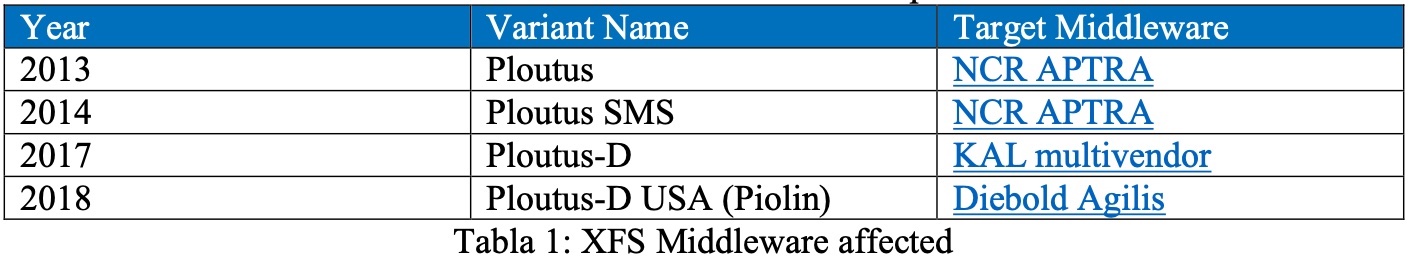 Versions of the Ploutus ATM malware and the middleware it targets
Versions of the Ploutus ATM malware and the middleware it targets
Ploutus-I, however, doesn’t target the Itautec middleware, but instead communicates directly with XFS to command the ATMs to disgorge cash, Metabase Q reports. It does this using an executable named “GG.exe,” which appears to be a legitimate Itautec tool to test the cash dispenser of an ATM.
Jackpotting ATMs using Ploutus-I is risky for two reasons: Someone has to visit and break into an ATM to install the malware, and then someone needs to visit the ATM to collect the cash.
To install Ploutus-I, the lock on the ATM has to be breached. Then the hard drive of the ATM has to be removed and connected to a laptop with the malware.
The malware is then copied into a specific file path, C:itautec. That path is for files that have been whitelisted from antivirus, thus insulating Ploutus-I from quarantine, and the executable itself is deceptively named the “Itautec Protection Agent.”
An Attack in Action
It’s possible that the same person could both install the malware and do the cash out. But usually, the Ploutus gang offers a one-time “license” to someone, known as a money mule, to do the cash out, Metabase Q says.
Cashing out requires connecting a keyboard to the ATM. This time around, however, investigators noticed that the keyboard appears within the operating system as a webcam rather than a keyboard. The cybercriminals apparently spoofed a keyboard as a webcam to deflect attention if anyone examined the operating system.
The keyboard is then used to enter a series of codes, including an activation code that eventually commands Ploutus to send the command to the XFS middleware to dispense money, Metabase Q reports.
“As expected, the gang knows exactly the ATM version they are targeting and its physical capabilities, and therefore the malware requested the maximum amount of bills to retrieve in every round, which in this case are 70, starting from the cassette with higher denomination, meaning $35,000 MXN ($1,677 USD) per round,” Jesus Dominguez from Metabase Q’s Ocelot Offensive Security Team writes in a technical report.
As part of the deal, the criminal group gets a cut, although it’s unclear how that physical transfer of money takes place with the mule.
In the bigger picture, financial institutions across Latin America don’t have a great record of information sharing, which would help defend against threats like Ploutus, Benavides says. They’re also lagging in cybersecurity best practices, he says.
To read the original article:
https://www.bankinfosecurity.com/ploutus-malware-targets-atms-in-latin-america-a-16087



