A new ransomware called ‘Hog’ encrypts users’ devices and only decrypts them if they join the developer’s Discord server.
This week, security researcher MalwareHunterTeam found an in-development decryptor for the Hog Ransomware that requires victims to join their Discord server to decrypt their files.
BleepingComputer was later able to find the encryptor component [VirusTotal] for the ransomware, which, when executed, will check if a particular Discord server exists, and if it does, begins to encrypt the victims’ files.
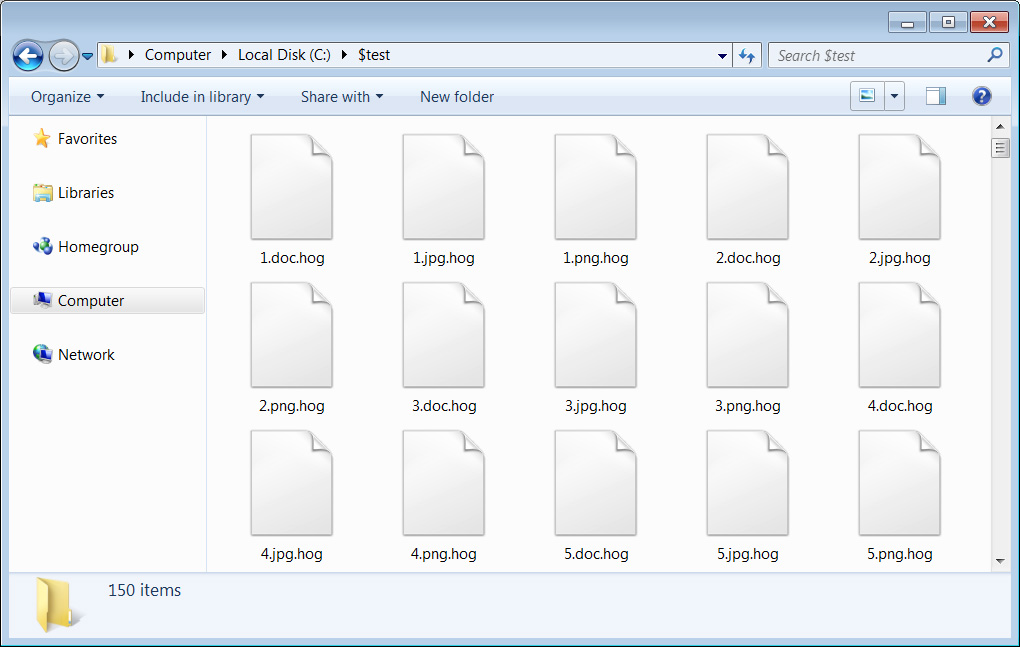
When encrypting a victims’ files, it will append the .hog extension as shown below and automatically extract the decryptor component.
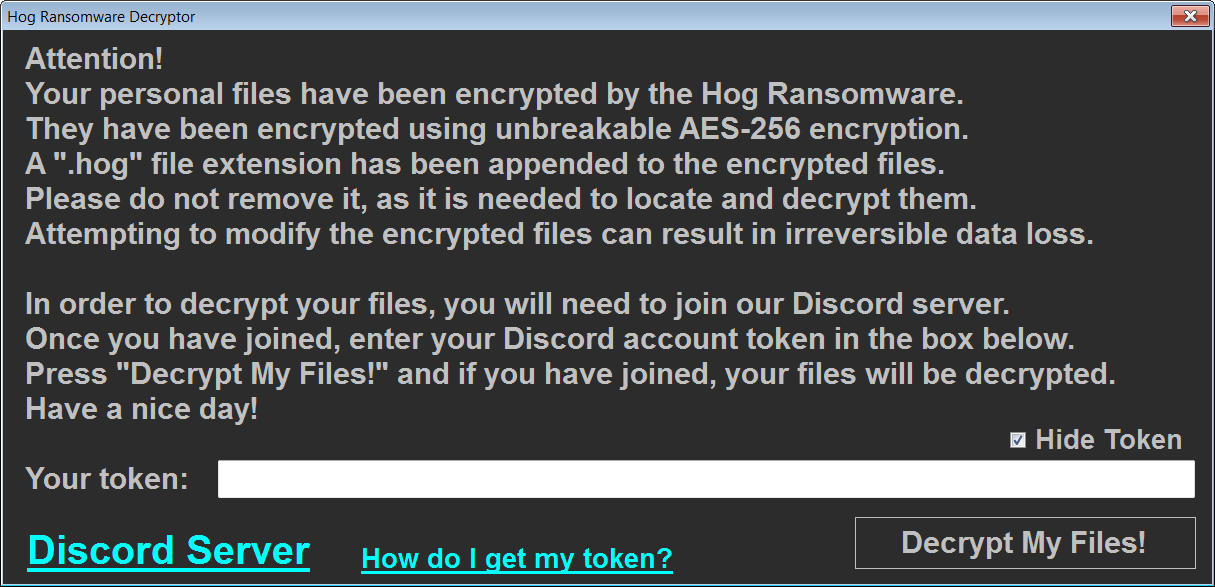
Once the ransomware has finished encrypting the device, it will launch the DECRYPT-MY-FILES.exe decryptor program from the Windows Startup folder.
This decryptor will explain what happened to the victims and then prompt them to enter their Discord user token.
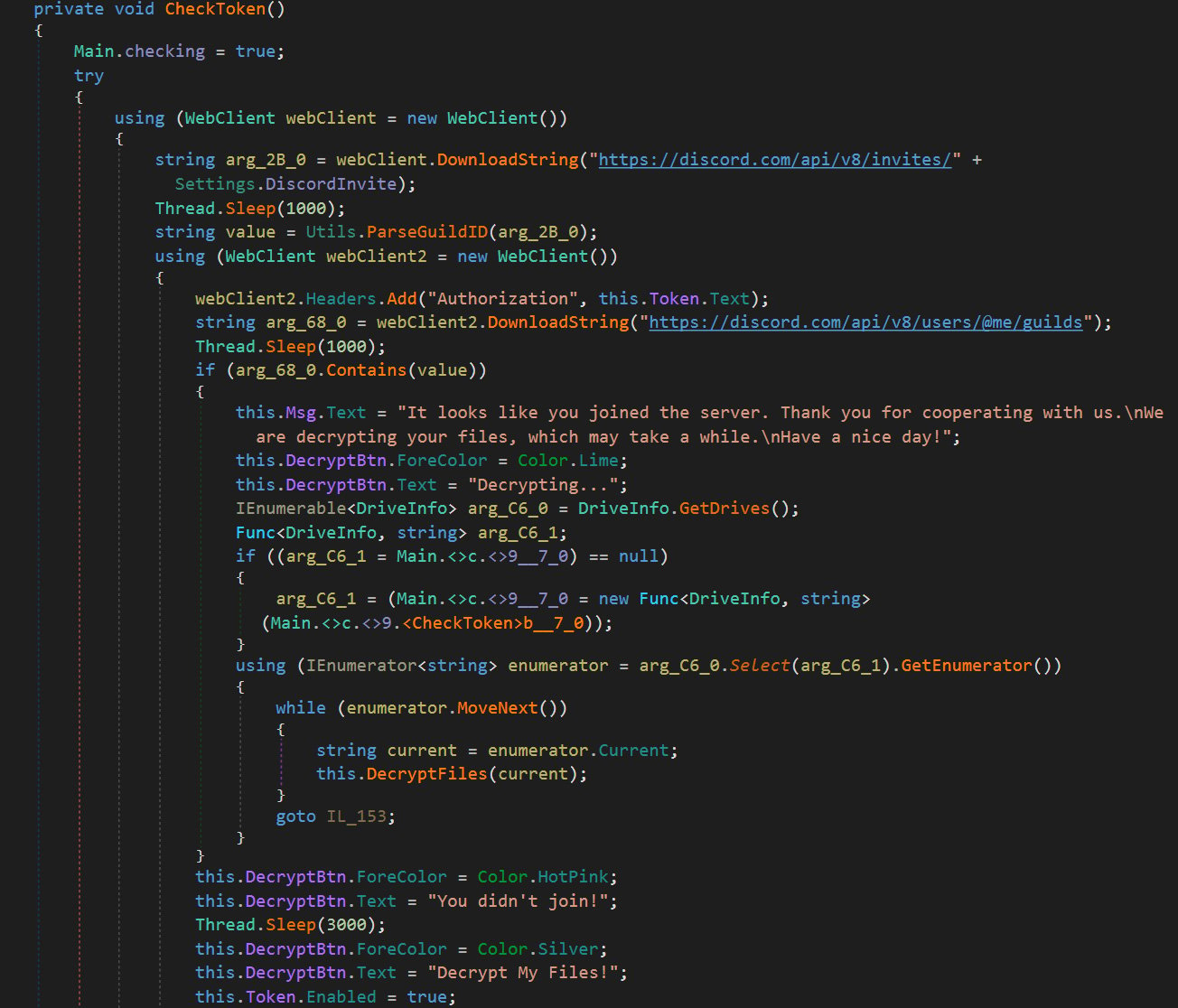
A Discord token allows the ransomware to authenticate to Discord’s APIs as the user and check if they joined their server, as shown by the source code below.
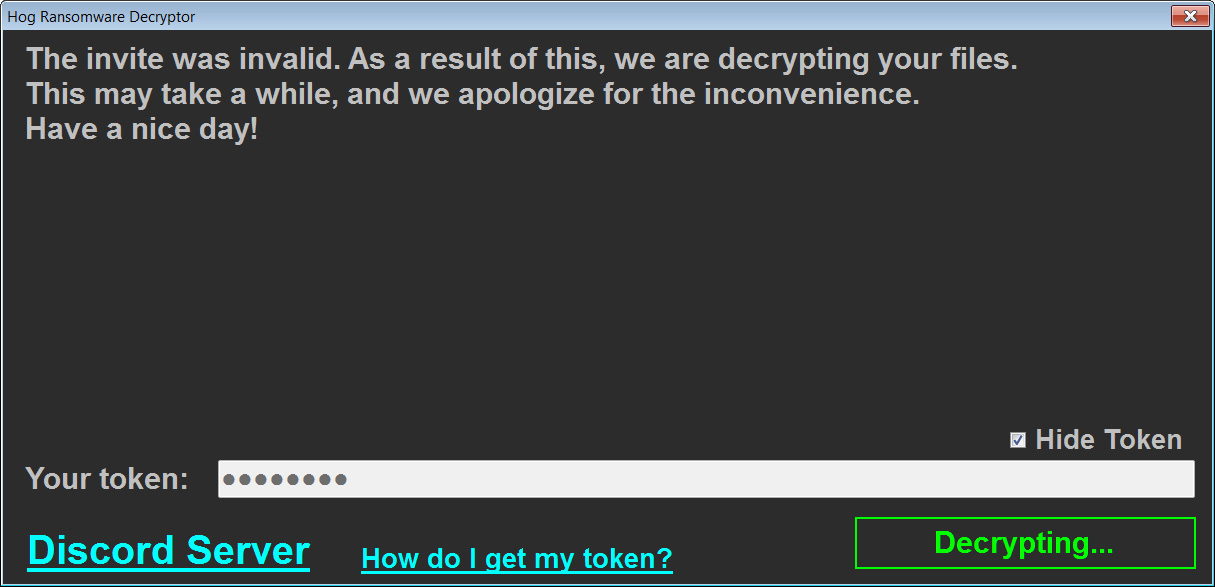
If the victim has joined the server or the server does not exist, the ransomware will decrypt the victims’ files using a static key embedded in the ransomware.
While this appears to be an in-development ransomware, it does illustrate how threat actors are beginning to use Discord more often for malicious activities.
Another ransomware known as Humble was recently discovered by Trend Micro that uses a webhook to post details about new victims to the threat actor’s Discord server.
Also, Discord is commonly used by threat actors to distribute malware or harvest stolen data.
As threat actors turn to Discord, it is critical for administrators and network security tools to monitor Discord traffic for threats or other abnormal behavior.
To read the original article:



