An ongoing phishing operation that stole an estimated 400,000 OWA and Office 365 credentials since December has now expanded to abuse new legitimate services to bypass secure email gateways (SEGs).
The attacks are part of multiple phishing campaigns collectively dubbed the “Compact” Campaign, active since early 2020 first detected by the WMC Global Threat Intelligence Team.
“Phishers continue to find success in using compromised accounts on email marketing services to send malicious emails from legitimate IP ranges and domains,” Microsoft’s security experts said.
“They take advantage of configuration settings that ensure delivery of emails even when the email solution detects phishing.”
Appspot now also abused to bypass SEGs
Attackers behind these phishing campaigns have stolen more than 400,000 stolen Office 365 and Outlook Web Access credentials since December, according to WMC Global.
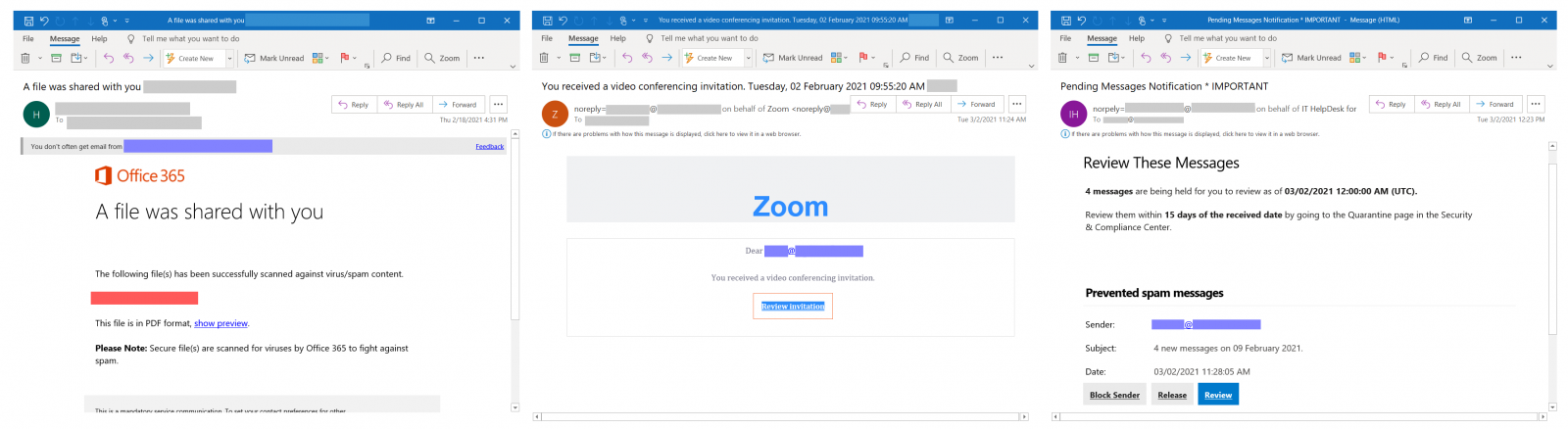
Their phishing emails are camouflaged as notifications from video conferencing services, various security solutions, and productivity tools to add legitimacy.
The threat actors also use compromised accounts for SendGrid and MailGun email delivery services, taking advantage of secure email gateways allow lists having them listed as trusted domains.
This allows the phishing messages to bypass them and land in the targets’ inboxes, luring them into clicking on embedded hyperlinks that redirect them to phishing landing pages designed to impersonate Microsoft login pages.
“In December, the landing page impersonated the Outlook Web App brand to trick targets into entering their credentials,” WMC Global said.
“In January, the attacks changed to mimic Office 365 brand, likely to capture more employee credentials.”
The phishing operation continues to expand as it now also abuses Amazon Simple Email Service (SES) and the Appspot cloud computing platform—used to develop and host web apps in Google-managed data centers—to deliver phishing emails and generate multiple phishing URLs for each target.
Domains and accounts used throughout this phishing campaign are being taken down as soon as Microsoft and WMC Global detect them.
“We shared our findings with Appspot, who confirmed the malicious nature of the reported URLs and used the shared intelligence to find and suspend additional offending projects on Appspot,” Microsoft added.
“Because this campaign uses compromised email marketing accounts, we strongly recommend orgs to review mail flow rules for broad exceptions that may be letting phishing emails through,” Microsoft advised.
To read the original article:



