Vast swathes of companies were likely compromised before patches were applied, so the danger remains.
The patching level for Microsoft Exchange Servers that are vulnerable to the ProxyLogon group of security bugs has reached 92 percent, according to Microsoft.
The computing giant tweeted out the stat earlier this week – though of course patching won’t fix already-compromised machines. Still, that’s an improvement of 43 percent just since last week, Microsoft pointed out (using telemetry from RiskIQ).
ProxyLogon consists of four flaws (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065) that can be chained together to create a pre-authentication remote code execution (RCE) exploit – meaning that attackers can take over servers without knowing any valid account credentials. This gives them access to email communications and the opportunity to install a web shell for further exploitation within the environment.
The good news on patching comes as a whirlwind of ProxyLogon cyberattacks has hit companies across the globe, with multiple advanced persistent threats (APT) and possibly other adversaries moving quickly to exploit the bug. A spate of public proof-of-concept exploits has added fuel to the fire – which is blazing so bright that F-Secure said on Sunday that hacks are occurring “faster than we can count,” with tens of thousands of machines compromised.
“To make matters worse, proof-of-concept automated attack scripts are being made publicly available, making it possible for even unskilled attackers to quickly gain remote control of a vulnerable Microsoft Exchange Server,” according to F-Secure’s writeup. “There is even a fully functioning package for exploiting the vulnerability chain published to the Metasploit application, which is commonly used for both hacking- and security testing. This free-for-all attack opportunity is now being exploited by vast numbers of criminal gangs, state-backed threat actors and opportunistic script kiddies.”
The attackers are using ProxyLogon to carry out a range of attacks, including data theft and the installation of malware, such as the recently discovered “BlackKingdom” strain. According to Sophos, the ransomware operators are asking for $10,000 in Bitcoin in exchange for an encryption key.
Patching Remains Tough for Many
The CyberNews investigation team found 62,174 potentially vulnerable unpatched Microsoft Exchange Servers around the world, as of Wednesday.
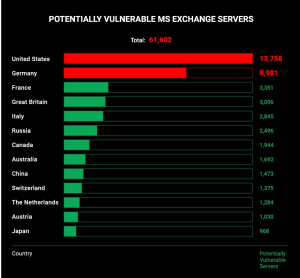
Click to enlarge. Source: CyberNews.
Victor Wieczorek, practice director for Threat & Attack Simulation at GuidePoint Security, noted that some organizations not structured or resourced to patch effectively against ProxyLogon.
“This is because, 1) a lack of accurate asset inventory and ownership information; and 2) lag time to vet patching for negative impacts on the business and gain approval from asset/business owners to patch,” he told Threatpost. “If you don’t have an accurate inventory with a high level of confidence, it takes a long time to hunt down affected systems. You have to determine who owns them and if applying the patch would negatively impact the system’s function. Responsible and timely patching takes lots of proactive planning and tracking.”
He added that by regularly testing existing controls (red-teaming), searching for indicators of existing weakness and active threats (threat hunting), and investing/correcting confirmed vulnerabilities (vulnerability management), organizations are going to be in a much better spot to adjust to emerging vulnerabilities and invoke their incident-response capabilities when needed.
APT Activity Continues
Microsoft said in early March that it had spotted multiple zero-day exploits in the wild being used to attack on-premises versions of Microsoft Exchange servers.
And indeed, Microsoft noted that adversaries from a Chinese APT called Hafnium were able to access email accounts, steal a raft of data and drop malware on target machines for long-term remote access. It’s also apparent that Hafnium isn’t the only party of interest, according to multiple researchers; ESET said earlier in March that at least 10 different APTs are using the exploit.
The sheer volume of APTs mounting attacks, most of them starting in the days before ProxyLogon became publicly known, has prompted questions as to the exploit’s provenance – and ESET researchers mused whether it was shared around the Dark Web on a wide scale.
The APTs seem mainly bent on cyberespionage and data theft, researchers said.
“These breaches could be occurring in the background, completely unnoticed. Only after months or years will it become clear what was stolen,” according to F-Secure. “If an attacker knows what they are doing, the data has most likely already been stolen or is being stolen right now.”
Several versions of the on-premise flavor of Exchange are vulnerable to the four bugs, including Exchange 2013, 2016 and 2019. Cloud-based and hosted versions are not vulnerable to ProxyLogon.
Patching is Not Enough; Assume Compromise
Unfortunately, installing the ProxyLogon security patches alone does not guarantee that a server is secure – an attacker may have breached it before the update was installed.
“Patching is like closing a door. Therefore, 92 percent of the doors have been closed. But the doors were open for a relatively long time and known to all the bad actors,” Oliver Tavakoli, CTO at Vectra, told Threatpost. “Identifying and remediating already compromised systems will be a lot harder.”
Brandon Wales, the acting director for the Cybersecurity and Infrastructure Security Agency (CISA), said during a webinar this week that “patching is not sufficient.”
“We know that multiple adversaries have compromised networks prior to patches being applied Wales said during a Cipher Brief webinar. He added, “You should not have a false sense of security. You should fully understand the risk. In this case, how to identify whether your system is already compromised, how to remediate it, and whether you should bring in a third party if you are not capable of doing that.”
How Businesses Can Protect Against ProxyLogon
Yonatan Amitay, Security Researcher at Vulcan Cyber, told Threatpost that a successful response to mitigate Microsoft Exchange vulnerabilities should consist of the following steps:
- Deploy updates to affected Exchange Servers.
- Investigate for exploitation or indicators of persistence.
- Remediate any identified exploitation or persistence and investigate your environment for indicators of lateral movement or further compromise.
“If for some reason you cannot update your Exchange servers immediately, Microsoft has released instructions for how to mitigate these vulnerabilities through reconfiguration — here, as they recognize that applying the latest patches to Exchange servers may take time and planning, especially if organizations are not on recent versions and/or associated cumulative and security patches,” he said. “Note that the mitigations suggested are not substitutes for installing the updates.”
Microsoft also has issued a one-click mitigation and remediation tool for small- and medium-sized businesses in light of the ongoing swells of attacks.
Vectra’s Tavakoli noted that the mitigation guides and tools Microsoft has supplied don’t necessarily help post-compromise – they are intended to provide mitigation in advance of fully patching the Exchange server.
“The end result of a compromise is reflective of the M.O. of each attack group, and that will be far more variable and less amenable to automated cleanup,” he said.
Milan Patel, global head of MSS for BlueVoyant, said that identifying follow-on malicious activity after the bad guys have gotten access to a network requires a good inventory of where data is housed.
“Incident response is a critical reactive tool that will help address what data could have been touched or stolen by the bad guys after they gained access to the critical systems,” he told Threatpost. “This is critical, this could mean the difference between a small cleanup effort vs. potential litigation because sensitive data was stolen from the network.”
To read the original article:
https://threatpost.com/microsoft-exchange-servers-proxylogon-patching/165001/



