Hancitor is an information stealer and malware downloader used by a threat actor designated as MAN1, Moskalvzapoe, or TA511.
Hancitor was noticed quite unsophisticated from 2018, but it remained a threat for years to come. Around three years later, Hancitor remains a threat and has evolved to use tools like Cobalt Strike.
In recent months, this actor began using a network ping tool to help enumerate the Active Directory (AD) environment of infected hosts.
Chain of Events for Recent Hancitor Infections
The chain of events for recent Hancitor infections is:
- An email with a link to a malicious page hosted on Google Drive.
- Link from a Google Drive page to a URL that returns a malicious Word document.
- Enable macros (per instructions in Word document text).
- Hancitor DLL is dropped and run using rundll32.exe.
- Hancitor generates command and control (C2) traffic.
- Hancitor C2 most often leads to Ficker Stealer malware.
- Hancitor C2 leads to Cobalt Strike activity in AD environments.
- Hancitor-related Cobalt Strike activity can send other files, such as a network ping tool or malware based on the NetSupport Manager Remote Access Tool (RAT).
- In rare cases, a Hancitor infection follow-up with Send-Safe spambot malware that turned an infected host into a spambot pushing more Hancitor-based malspam.
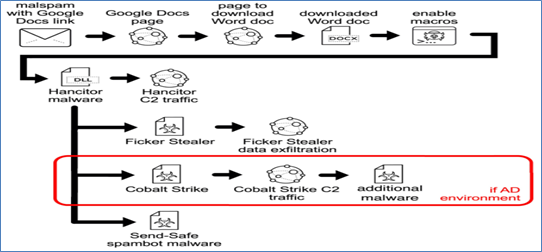
Hancitor chain of events
First Stage: Distributing Malicious Word Documents
Hancitor has historically sent emails spoofing different types of organizations that send notices, faxes or invoices. At present, most waves of emails pushing Hancitor have used a DocuSign theme.
These DocuSign-themed messages have links to malicious Google Drive pages established through fraudulent or possibly compromised Google accounts. Cloud-based collaborative services such as Microsoft’s OneDrive and Google Drive are frequently abused by threat actors to distribute malware.
Second Stage: Hancitor Infects Victim
When macros are enabled for these malicious Word documents, the macro code drops and runs a malicious DLL file for Hancitor. The DLL file is contained within the macro code. Network traffic caused by Hancitor starts with an IP address check by the infected Windows host.
The IP check is immediately followed by C2 traffic. Posted data also includes the version of Windows and domain information if the infected host is part of an AD environment. Finally, posted data also contains a Globally Unique Identifier (GUID) for the infected host and a build number for the Hancitor malware sample.
Third Stage: Hancitor Retrieves Follow-Up Malware
After Hancitor establishes C2 traffic, it retrieves follow-up malware. Each day, follow-up malware items for Hancitor are hosted on the same domain. Hancitor will only send Cobalt Strike when it infects a host in an AD environment.
Final Stage: Cobalt Strike Sends Malware
Cobalt Strike is used by the threat actor behind Hancitor to send follow-up malware. Another file that appeared on Hancitor-infected hosts after Cobalt Strike started as a Windows EXE file for a network ping tool. The network ping tool was always saved to the same directory as the Hancitor Word document.
This ping tool is designed to find any other active hosts within an AD environment. The tool generates approximately 1.5 GB of ICMP ping traffic over the network as it pings more than 17 million IP addresses of internal, non-routable IPv4 address space.
Therefore, organizations with decent spam filtering, proper system administration, and up-to-date Windows hosts have a much lower risk of infection from Hancitor and its post-infection activity. Palo Alto Networks Next-Generation Firewall customers are further protected from this threat with a Threat Prevention security subscription.
To read the original article:
https://cybersecuritynews.com/hancitor-malware-network-attacks/



