$50 Million Extortion Demand Issued to Apple and Taiwanese Manufacturer Quanta
The REvil – aka Sodinokibi – ransomware gang is threatening to release stolen Apple device blueprints unless it receives a massive payoff.
The extortion threat was unveiled Tuesday, hours before Apple was scheduled to make a series of major new product announcements. REvil published a number of alleged blueprints for Apple devices, which it claimed to have stolen from Taiwanese manufacturer Quanta Computer, which builds computing devices for a number of vendors.
“In order not to wait for the upcoming Apple presentations, today we, the REvil group, will provide data on the upcoming releases of the company so beloved by many,” the REvil gang says in a post to its data leak site. “Tim Cook can say thank you Quanta,” it adds, referring to Apple’s CEO.
REvil claims that its previous ransom demands have been rebuffed by Quanta. “From our side, a lot of time has been devoted to solving this problem. Quanta has made it clear to us that it does not care about the data of its customers and employees, thereby allowing the publication and sale of all data we have,” REvil says.
Quanta and Apple didn’t immediately respond to a request for comment.
REvil’s data-leak site further lists Cisco, Dell, HP, Siemens, Sony and Toshiba as being among the other manufacturers with which Quanta works. This information appears has been copied and pasted from the Wikipedia page for Quanta Computer, at least some of which is inaccurate. “We do not have a relationship with Quanta Computer,” a Dell spokeswoman tells Information Security Media Group.
 REvil copied the information contained in its data-leak site post from the Wikipedia page for Quanta Computer, which lists a number of manufactures as customers. But Dell says it has no “relationship with Quanta Computer.”.
REvil copied the information contained in its data-leak site post from the Wikipedia page for Quanta Computer, which lists a number of manufactures as customers. But Dell says it has no “relationship with Quanta Computer.”.
Extortion Demands
REvil on Tuesday began releasing a series of “proofs” that appear to show blueprints and designs for products. The gang’s data leak site references Apple Watch, MacBook Air, MacBook Pro and the ThinkPad Z60m. The latter appears to be a Lenovo device produced in the early 2000s.
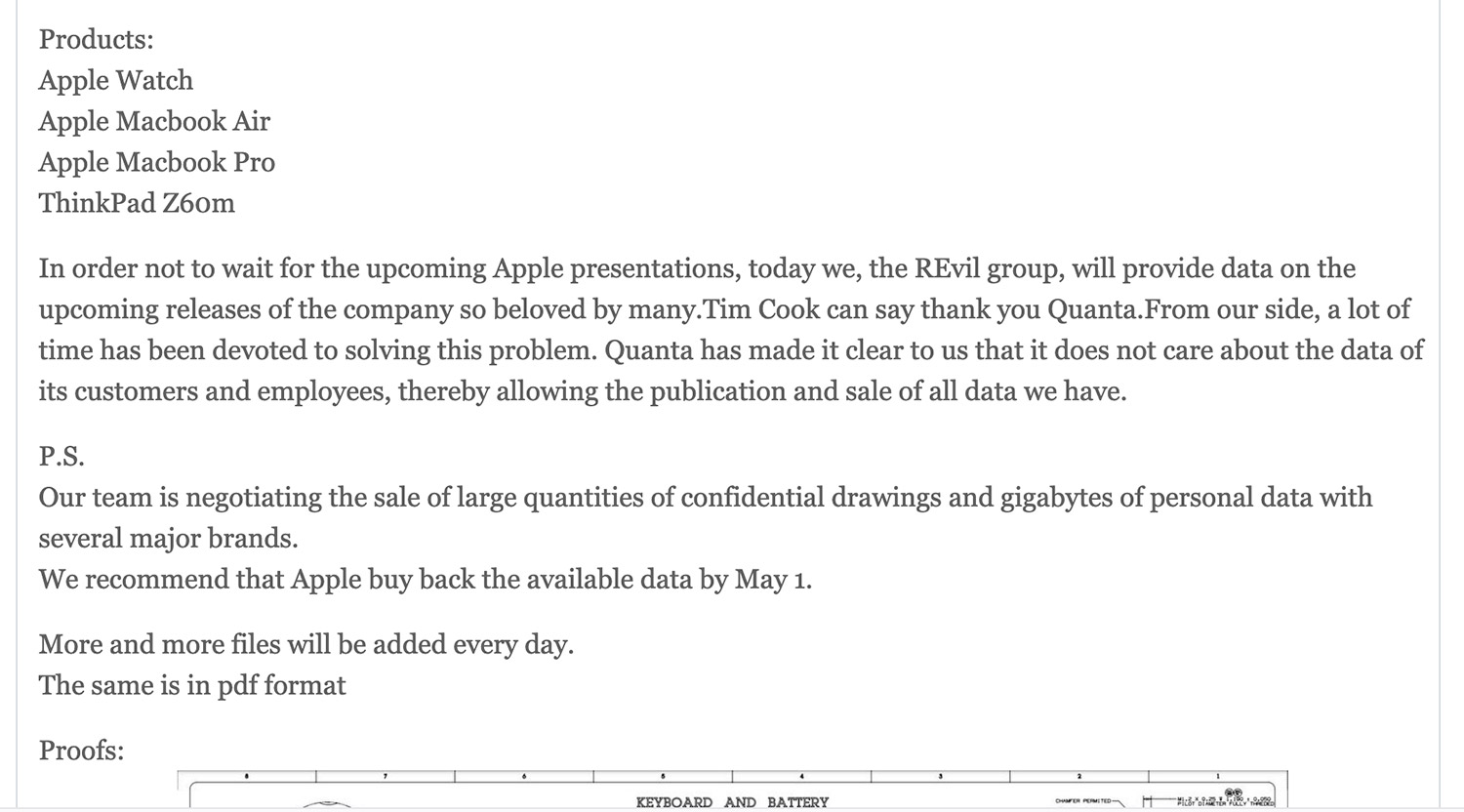 Excerpt from REvil’s Quanta listing on its data leak site, which mixes information copied from Wikipedia with extortionist bluster
Excerpt from REvil’s Quanta listing on its data leak site, which mixes information copied from Wikipedia with extortionist bluster
In fact, the four devices – or device ranges – listed by REvil have also been copied from the Wikipedia page for Quanta Computer, which lists only those four products as examples of what Quanta manufactures.
Attempting to up the pressure on Quanta and Apple to pay a ransom, REvil notes: “Our team is negotiating the sale of large quantities of confidential drawings and gigabytes of personal data with several major brands. We recommend that Apple buy back the available data by May 1.”
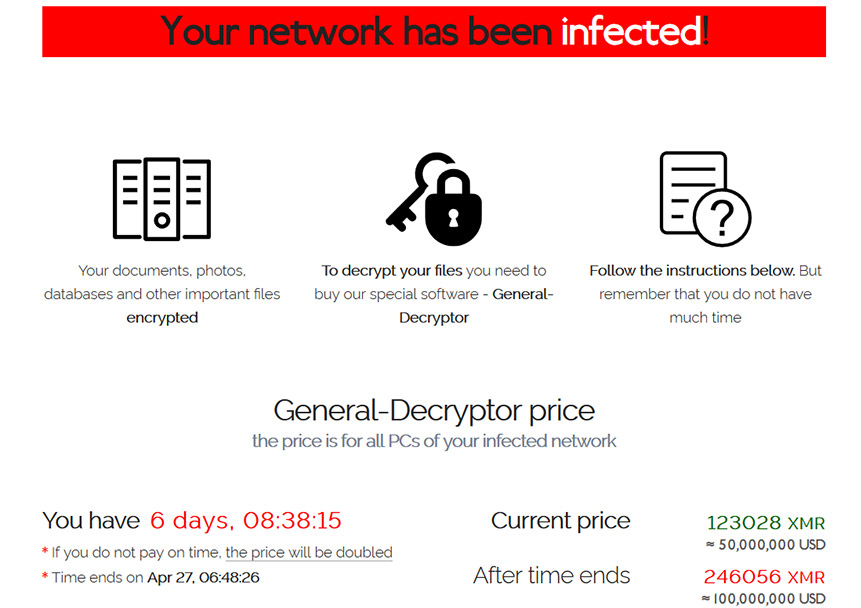 REvil’s ransom demand note to Quanta (Source: Bleeping Computer)
REvil’s ransom demand note to Quanta (Source: Bleeping Computer)
Apple news site 9to5Mac says the information leaked so far appears to be legitimate, but also “deeply technical, including power voltage specifications and other nitty gritty details” for two forthcoming models of Apple Silicon MacBook Pro.
REvil’s ransom demand to Quanta is $50 million if paid by April 27, doubling to $100 million afterward, reports Bleeping Computer, which obtained a copy of the ransom note. It also obtained communications between REvil and Quanta in which the ransomware gang claims that it has also obtained data pertaining to Apple’s employees and customers.
Negotiating Tactics
Many ransomware gangs, especially if they practice big game hunting – meaning they deliberately target larger organizations, seeking higher ransom payoffs – often open their ransom demands with a large sum so they can allow it to be negotiated down later.
REvil is one of the most prolific ransomware-as-a-service operations. Such operations involve an operator providing crypto-locking malware, and support, to vetted affiliates, who infect victims’ systems with the malware. For every victim who pays, the operator takes a cut. For REvil, at least historically, this cut has started at 40%, dropping to 30% after an affiliate racks up three successful ransom payments. Many RaaS operators also maintain a data leak site where affiliates can post stolen data (see: Sodinokibi Ransomware Gang Appears to Be Making a Killing).
After attempting to name and shame victims via dedicated data leak sites, many ransomware gangs then begin leaking data. If a victim still doesn’t pay, then the gang typically dumps all of the stolen data for free in an attempt teach future victims a lesson. Many gangs also claim to be negotiating sales to other interested parties or auctioning stolen data to the highest bidder, although it’s not clear to what extent this ever comes to pass.
REvil has recently been targeting a number of large firms, including Taiwan-based Acer. As Bleeping Computer first reported last month, Acer also received a $50 million ransom demand.
“When groups make enormous demands like this, I’m not sure they actually expect to be paid – at least not their full ask,” Brett Callow, a security threat analyst at security firm Emsisoft, told Information Security Media Group at the time. “To my mind, it’s far more likely that the demand is intended to encourage companies to up their policy limits and make them feel lucky – and so more likely to pay – when they get hit with a ‘modest’ demand of $10 million.”
Apple’s Product Launch Proceeds
On Tuesday, at a virtual event, Cook and others unveiled a slew of new Apple products, including a new iPad Pro, iMac desktop computer and Apple TV as well as the availability of the existing iPhone 12 and iPhone 12 mini in a new, springtime color: purple.
 Apple announced the launch of an iPhone 12 and iPhone 12 mini in purple. (Source: Apple)
Apple announced the launch of an iPhone 12 and iPhone 12 mini in purple. (Source: Apple)
Apple also announced the launch of AirTag, a small accessory designed to help users find lost items, such as car keys.
Apple says the devices will use the “find my network” built into iOS, “all while keeping location data private and anonymous with end-to-end encryption.” The devices use a battery that will need to be replaced approximately every year, Apple says. The tags will compete with existing devices – from such vendors as Tile and Chipolo – that offer the ability to find lost items, albeit without such functionality being baked into Apple’s mobile operating system.
Senate Antitrust Hearing Looms
Tile has been a vocal opponent of Apple duplicating functionality built by others into its operating system, and its CEO, CJ Prober, is set to testify Wednesday at a Senate Judiciary Committee antitrust hearing into whether Apple and Google’s app stores unfairly restrict competition.
Executives from Apple and Google are also slated to testify at the hearing, as are executives from dating service Match and music-streaming service Spotify, who have criticized Apple for the cut it takes from all sales made via its App Store, Reuters reports.
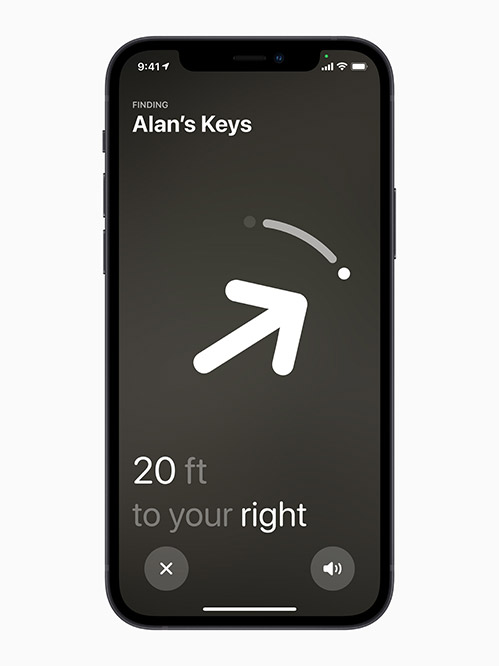 Apple says its new AirTag device, designed to help users locate lost items, uses end-to-end encryption to help keep user data – and device locations – private and anonymized to others.
Apple says its new AirTag device, designed to help users locate lost items, uses end-to-end encryption to help keep user data – and device locations – private and anonymized to others.“We think it is entirely appropriate for Congress to take a closer look at Apple’s business practices specific to its entry into this category,” Tile’s Prober says in a statement. “We welcome competition, as long as it is fair competition. … Unfortunately, given Apple’s well-documented history of using its platform advantage to unfairly limit competition for its products, we’re skeptical.”
Apple tells Reuters that it recently allowed third-party trackers to work with iOS in a manner designed to comply with its user and device privacy standards.
In a statement shared with The Wall Street Journal, Apple further defended its approach.
“We have always embraced competition as the best way to drive great experiences for our customers, and we have worked hard to build a platform in iOS that enables third-party developers to thrive,” an Apple spokesman said.
To read the original article:
https://www.bankinfosecurity.com/revil-ransomware-gang-threatens-stolen-apple-blueprint-leak-a-16441



