A staggering number of 3.28 billion passwords linked to 2.18 billion unique email addresses were exposed in what’s one of the largest data dumps of breached usernames and passwords.
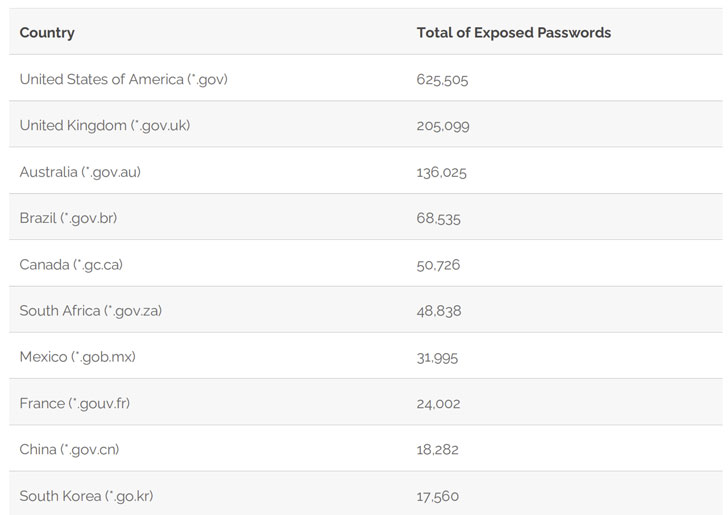
In addition, the leak includes 1,502,909 passwords associated with email addresses from government domains across the world, with the U.S. government alone taking up 625,505 of the exposed passwords, followed by the U.K (205,099), Australia (136,025), Brazil (68,535), and Canada (50,726).
The findings come from an analysis of a massive 100GB data set called “COMB21” — aka Compilation of Many Breaches — that was published for free in an online cybercrime forum earlier this February by putting together data from multiple leaks in different companies and organizations that occurred over the years.
It’s worth noting that a leak doesn’t imply a breach of public administration systems. The passwords are said to have been obtained via techniques such as password hash cracking after being stolen or through phishing attacks and eavesdropping on insecure, plaintext connections.
The top 10 U.S. government domains affected by the leak are as follows:
- State Department – state.gov (29,144)
- Veterans Affairs Department – va.gov (28,937)
- Department of Homeland Security – dhs.gov (21,575)
- National Aeronautics and Space Administration – nasa.gov (15,665)
- Internal Revenue Service – irs.gov (10,480)
- Center for Disease Control and Prevention – cdc.gov (8,904)
- Department of Justice – usdoj.gov (8,857)
- Social Security Administration – ssa.gov (8,747)
- U.S. Postal Service – usps.gov (8,205), and
- Environmental Protection Agency – epa.gov (7,986)
Interestingly, this leak also includes 13 credentials linked to emails of the Oldsmar water plant in Florida, as previously reported by CyberNews. However, there’s no evidence that the breached passwords were to carry out the cyberattack in February. In contrast, only 18,282 passwords related to Chinese government domains and 1,964 passwords from those related to Russia were laid bare.
“It is an indication that the passwords in these countries, made up of local alphabets, are less targeted by hackers. It is an unexpected layer of protection in relation to the Roman alphabet,” said Syhunt Founder and Chief Visionary Officer (CVO) Felipe Daragon.
On a related note, a notorious threat actor named ShinyHunters has posted an alleged database consisting of 20 million BigBasket users for free, almost five months after the Indian online grocery delivery startup confirmed a data breach. According to Under the Breach’s Alon Gal, the database includes users’ email addresses, phone numbers, residential addresses, hashed passwords, dates of birth, and order histories.
In the past, ShinyHunters has been connected to the sale of personal data from several companies, including Zoosk, SocialShare, Tokopedia, TeeSpring, Mindful, Minted, Chatbooks, Dave, Promo, Mathway, Wattpad, MeetMindful.com, and StarTribune.
Users who have had their information exposed are strongly advised to change their existing passwords.
To read the original article:
https://thehackernews.com/2021/04/32-billion-leaked-passwords-contain-15.html