Apple has fixed a zero-day vulnerability in macOS exploited in the wild by Shlayer malware to bypass Apple’s File Quarantine, Gatekeeper, and Notarization security checks and download second-stage malicious payloads.
Shlayer’s creators have managed to get their malicious payloads through Apple’s automated notarizing process before.
If they pass this automated security check, macOS apps are allowed by Gatekeeper—a macOS security feature that verifies if downloaded apps have been checked for known malicious content—to run on the system.
In the past, Shlayer also used a two-year-old technique to escalate privileges and disable macOS’ Gatekeeper to run unsigned second-stage payloads in a campaign detected by Carbon Black’s Threat Analysis Unit.
Zero-day exploited in the wild to deploy malware
The Jamf Protect detection team discovered that starting January 2021, the Shlayer threat actors created unsigned and unnotarized Shlayer samples have begun exploiting a zero-day vulnerability (tracked as CVE-2021-30657), discovered and reported to Apple by security engineer Cedric Owens.
As revealed by security researcher Patrick Wardle, this now fixed bug takes advantage of a logic flaw in the way Gatekeeper checked if app bundles were notarized to run on fully-patched macOS systems.
Wardle added that “this flaw can result in the misclassification of certain applications, and thus would cause the policy engine to skip essential security logic such as alerting the user and blocking the untrusted application.”
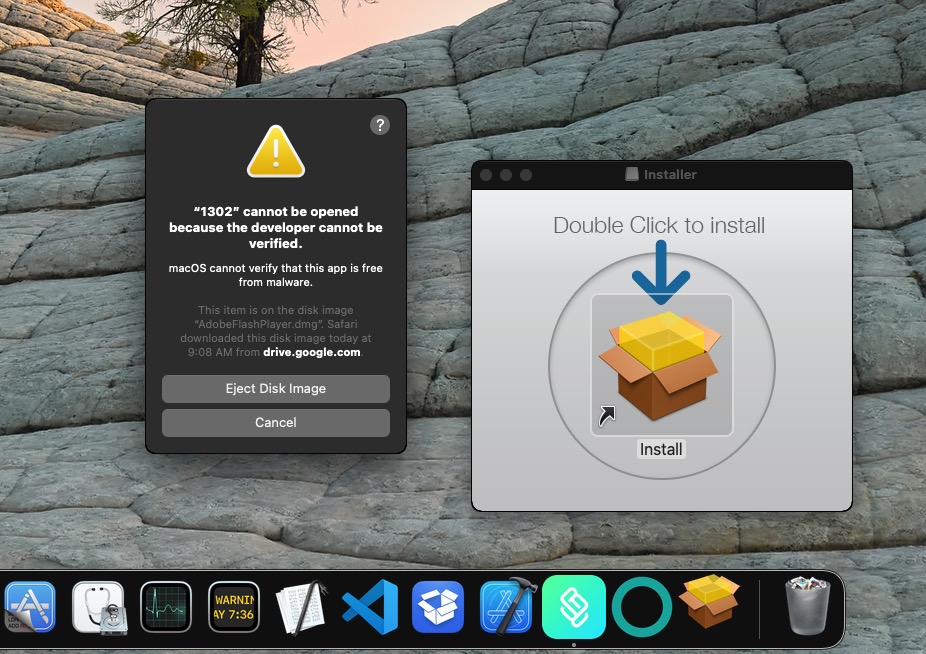
Unlike previous variants that required victims to right-click and then open the installer script, recent malware variants abusing this zero-day and distributed using poisoned search engine results and compromised websites can be launched by double-clicking.
Today, Apple has released a security update to fix the vulnerability in macOS Big Sur 11.3 and block malware campaigns actively abusing it.
Users are now alerted that malicious apps “cannot be opened because the developer cannot be identified” and advised to eject the mounted disk image because it may contain malware.
The Shlayer macOS malware
Shlayer is a multi-stage trojan that attacked over 10% of all Macs, according to a Kaspersky report from January 2020.
Intego’s research team spotted Shlayer for the first time in a malware campaign in February 2018, camouflaged as a fake Adobe Flash Player installer just as many other malware families targeting macOS users.
Unlike original variants, which were pushed via torrent sites, new Shlayer samples are now spread via fake update pop-ups shown on hijacked domains or clones of legitimate sites, or in far-reaching malvertising campaigns plaguing legitimate websites.
After infecting a Mac, Shlayer installs the mitmdump proxy software and a trusted certificate to analyze and modify HTTPS traffic, allowing it to monitor the victims’ browser traffic or inject ads and malicious scripts in visited sites.
Even worse, this technique allows the malware to alter encrypted traffic, such as online banking and secure email.
While Shlayer’s creators currently only deploy only adware as a secondary payload, they can quickly switch to more dangerous payloads such as ransomware or wipers at any time.
One more zero-day exploited in the wild fixed today
Today, the company another WebKit Storage zero-day bug exploited in the wild, tracked as CVE-2021-30661, and impacting iOS and watchOS devices by improving memory management.
The vulnerability allows attackers to execute arbitrary code after tricking targets into opening a maliciously crafted website on their devices.
The list of affected devices includes those running:
- Apple Watch Series 3 and later
- iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)
In total, with today’s security updates for macOS and iOS bugs exploited in the wild, Apple has addressed nine zero-days since November.
The company patched three other iOS zero-days—a remote code execution bug (CVE-2020-27930), a kernel memory leak (CVE-2020-27950), and a kernel privilege escalation flaw (CVE-2020-27932)—affecting iPhone, iPad, and iPod devices in November.
In January, Apple fixed a race condition bug in the iOS kernel (tracked as CVE-2021-1782) and two WebKit security flaws (tracked as CVE-2021-1870 and CVE-2021-1871).
To read the original aritcle:



