Pacific City Bank (PCB), one of the largest Korean-American community banking service providers in America, has disclosed a ransomware incident that took place last month.
The bank is circulating notices to inform its clients of a security breach it identified on August 30, 2021, which they claim to have addressed promptly.
Sensitive details leaked
PCB’s internal investigation on what happened was concluded on September 7, 2021, and it revealed that ransomware actors had unfortunately obtained the following information from its systems:
- Loan application forms
- Tax return documents
- W-2 information of client firms
- Payroll records of client firms
- Full names
- Addresses
- Social Security Numbers
- Wage and tax details
As PCB clarifies, not all clients have been impacted the same, as each customer has provided different documents and details that were stored in the compromised systems.
Also, whether or not this incident affects the entire clientele of the bank or just a small subset has not been determined. We have reached out to the bank for clarifications, but we have not heard back yet.
The recipients of these notices are advised to remain vigilant against incoming communications and monitor their financial account statements and credit reports for signs of fraud.
Additionally, the bank is offering one year of free credit monitoring and identity theft protection services through Equifax, with instructions on how to enroll enclosed in the letters. Follow these instructions without deviation to avoid getting scammed by actors who may attempt to seize the opportunity.
An AvosLocker victim
While Pacific City Bank did not reveal the name of the ransomware group behind the September incident, AvosLocker is claiming the attack and has published an entry on their data leak site
The date of the incident is set on September 4, 2021, so the five days of difference may just be the “grace” period of the initial negotiation round, during which ransomware actors typically avoid making announcements.
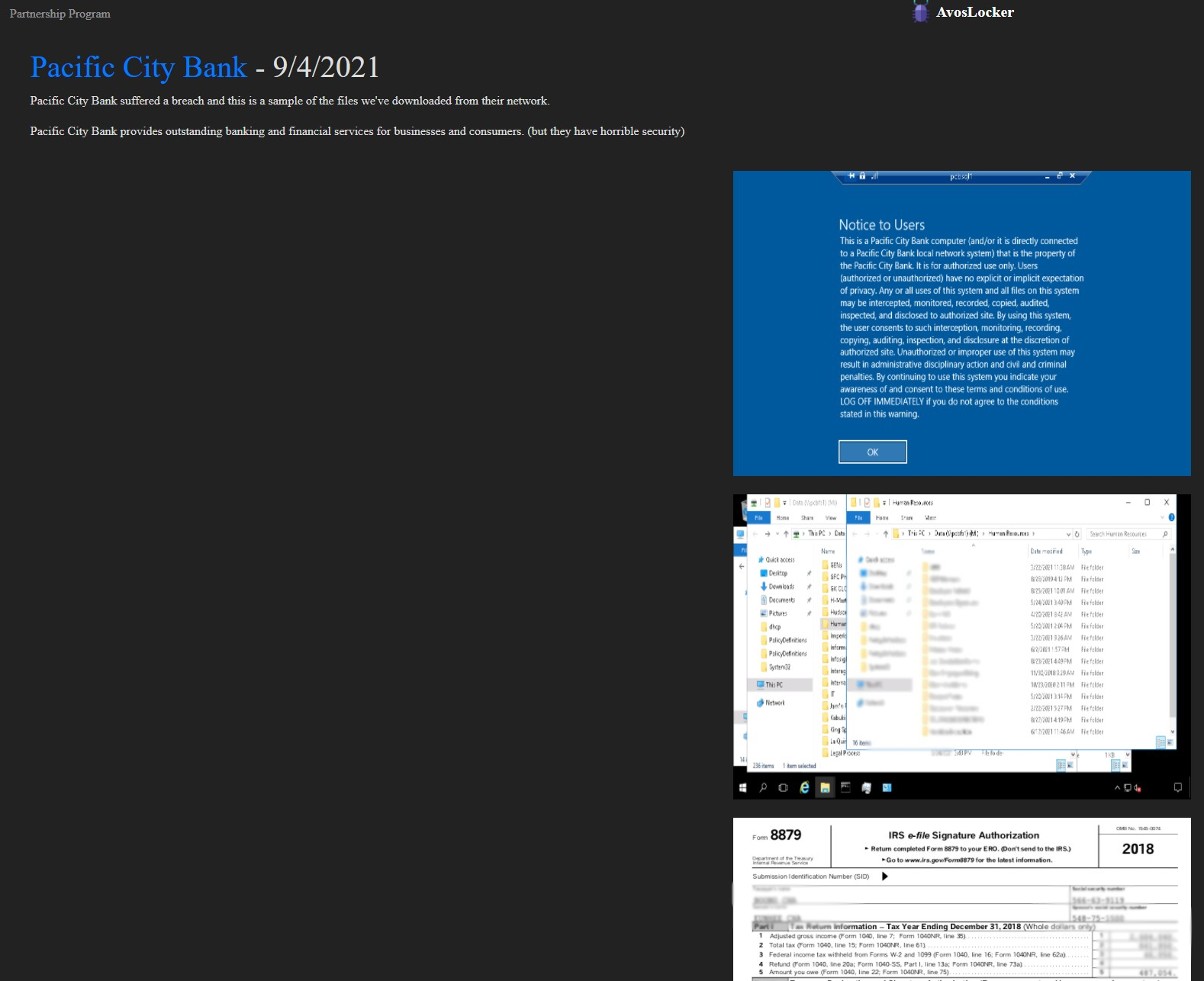
The files that were eventually posted on the extortion portal are showing what PCB has now admitted as compromised, so there are no disparities there.
AvosLocker is one of the newer ransomware operators, appearing in the wild this summer, calling for affiliates on various underground forums to join the RaaS.
The group uses a multi-threaded ransomware strain that enables them to encrypt files fast, while the payload is deployed manually by the attacker. Although the AvosLocker features some string and API obfuscation to evade static detection, it is generally “naked”, coming without a crypting layer.
For more details on the AvosLocker and what you can do if you’re hit by this ransomware family, check out our support topic.



