A new version of a Linux crypto-mining malware previously used to target Docker containers in 2020 now focuses on new cloud service providers like the Huawei Cloud.
The analysis of the new campaign comes from researchers at TrendMicro, who explains how the malware has evolved with new features while retaining its previous functionality.
More specifically, the newer samples have commented out the firewall rules creation function (but it’s still there) and continue to drop a network scanner to map other hosts with API-relevant ports.
However, the new malware version only targets cloud environments and is now seeking out and removing any other cryptojacking scripts that may have previously infected the system.
When infecting a Linux system, the malicious coinminer will perform the following steps, which include the removal of users creating by competing crypto-mining malware distributors.
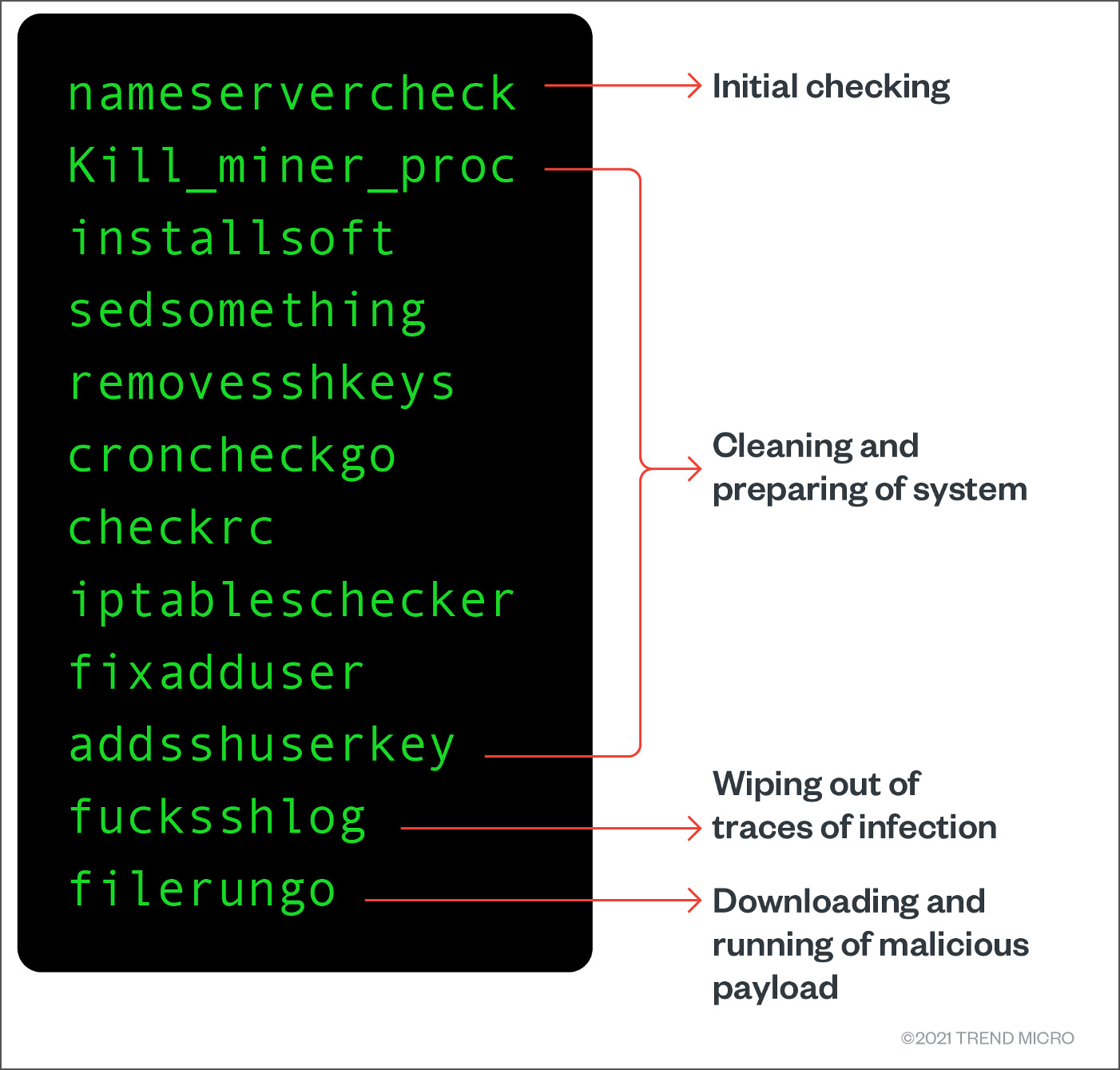
Source: Trend Micro
After removing users created by other threat actors, the actors add their own users, a common step for many cloud-targeting cryptojackers. However, unlike many other cryptominers, the malware adds their user accounts to the sudoers list, giving them root access to the device.
To ensure that persistence is maintained on the device, the attackers use their own ssh-RSA key to perform system modifications and change the file permissions to a locked state.
This means that even if another actor gains access to the device in the future, they won’t be able to take complete control of the vulnerable machine.
The actors install the Tor proxy service to protect communications from network scanning detection and scrutiny, passing all connections through it for anonymization.
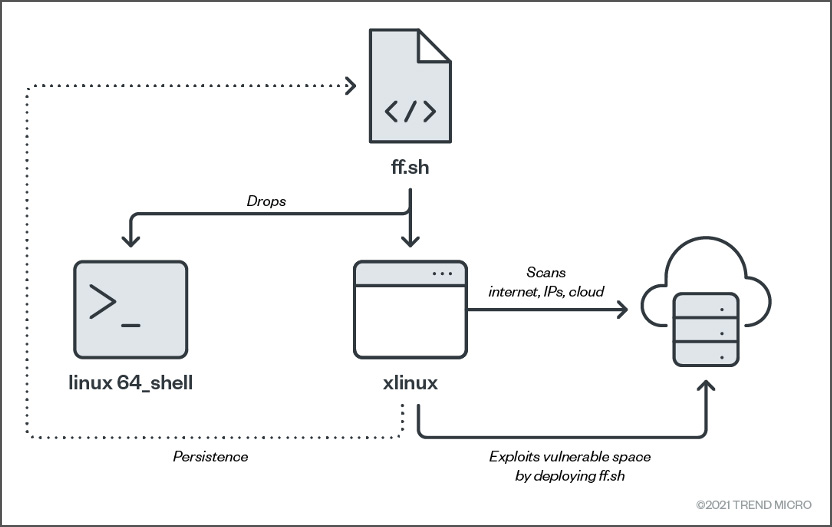
Source: TrendMicro
The binaries that are dropped (“linux64_shell”, ”ff.sh”, “fczyo”, “xlinux”) feature some level of obfuscation, and TrendMicro has seen signs of the UPX packer having been deployed for the wrapping.

Source: TrendMicro
The actors have gone through further tampering to tune the binaries for stealthiness against automated analysis and detection toolsets.
After gaining a foothold on a device, the hacker’s scripts will exploit remote systems and infect them with the malicious scripts and cryptominer.
The known vulnerabilities scanned during this attack include:
- SSH weak passwords
- Vulnerability in the Oracle WebLogic Server product of Oracle Fusion Middleware (CVE-2020-14882)
- Redis unauthorized access or weak passwords
- PostgreSQL unauthorized access or weak password
- SQLServer weak password
- MongoDB unauthorized access or weak password
- File transfer protocol (FTP) weak password
CSP under bombardment
Huawei Cloud is a relatively new service, but the Chinese tech giant claims it’s already serving over three million customers. TrendMicro has informed Huawei of the campaign, but they haven’t received an acknowledgment yet.
Whether you deploy your instances, keep in mind that running vulnerability assessments and malware scans may not be enough to defend against this attack. You need to evaluate your CSP’s security model and adjust your approach to complement it with further protections.
These cloud-targeting crypto miners have been on the rise since the beginning of the year, and as long as crypto values are soaring, actors will have an incentive to make them more powerful and harder to detect.
To read the original article: https://www.bleepingcomputer.com/news/security/huawei-cloud-targeted-by-updated-cryptomining-malware/



