Microsoft has published an advisory regarding a security feature bypass vulnerability impacting Surface Pro 3 tablets which could allow threat actors to introduce malicious devices within enterprise environments.
The security flaw tracked as CVE-2021-42299 can be exploited in high complexity attacks dubbed TPM Carte Blanche by Google security researchers who discovered them and shared additional details on Monday.
To successfully abuse the bug, attackers would either need access to the owner’s credentials or physical access to the device.
Bypass security integrity checks
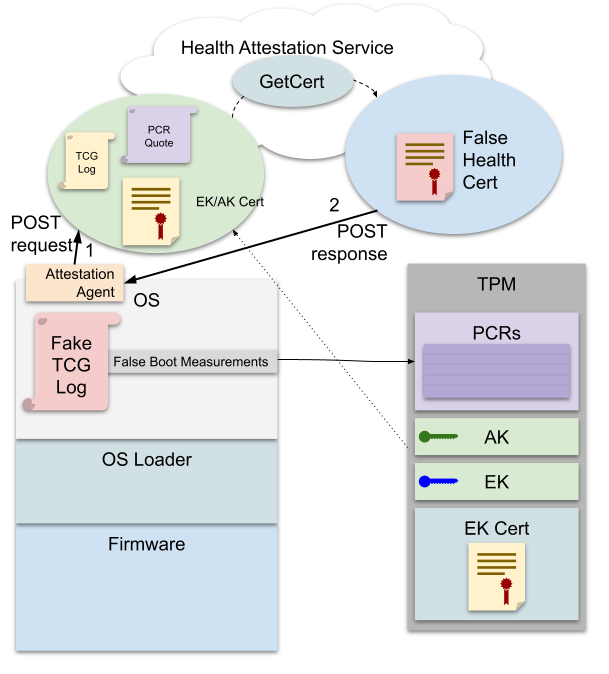
Device Health Attestation is a cloud and on-premises service that validates TPM and PCR logs for endpoints and informs Mobile Device Management (MDM) solutions if Secure Boot, BitLocker, and Early Launch Antimalware (ELAM) are enabled, Trusted Boot is correctly signed, and more.
By exploiting CVE-2021-42299, attackers can poison the TPM and PCR logs to obtain false attestations, allowing them to compromise the Device Health Attestation validation process.
“Devices use Platform Configuration Registers (PCRs) to record information about device and software configuration to ensure that the boot process is secure. Windows uses these PCR measurements to determine device health,” Microsoft explains.
“A vulnerable device can masquerade as a healthy device by extending arbitrary values into Platform Configuration Register (PCR) banks.”
“The attacker can prepare a bootable Linux USB stick to minimize the interactions required with the target device (e.g., as an Evil Maid attack),” added Chris Fenner, the Google software engineer who found the bug.
Devices from other vendors also vulnerable
Fenner also published proof-of-concept (Poc) exploit code demonstrating how the flaw could be exploited on Monday.
Microsoft confirmed Fenner’s findings that the Surface Pro 3 is exposed to TPM Carte Blanche attacks. More recent Surface devices such as the Surface Pro 4, Surface Book are not vulnerable.
While the Surface Pro 3 was released in June 2014 and discontinued in November 2016, Redmond says devices from other vendors could also be vulnerable to TPM Carte Blanche attacks and that it attempted to notify all affected vendors of the issue.
“It is possible that other devices, including non-Microsoft devices, using a similar BIOS may also be vulnerable,” Microsoft said.
Correction October 19, 11:45 EST: Updated story and title to remove Microsoft security updates info.
To read the original article:



