Cybersecurity researchers disclosed details of what they say is the “largest botnet” observed in the wild in the last six years, infecting over 1.6 million devices primarily located in China, with the goal of launching distributed denial-of-service (DDoS) attacks and inserting advertisements into HTTP websites visited by unsuspecting users.
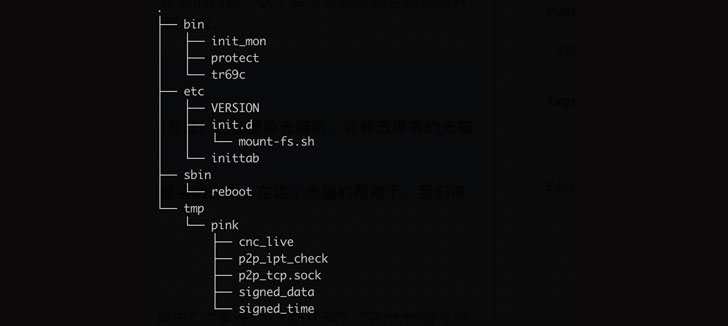
Qihoo 360’s Netlab security team dubbed the botnet “Pink” based on a sample obtained on November 21, 2019, owing to a large number of function names starting with “pink.”
Mainly targeting MIPS-based fiber routers, the botnet leverages a combination of third-party services such as GitHub, peer-to-peer (P2P) networks, and central command-and-control (C2) servers for its bots to controller communications, not to mention completely encrypting the transmission channels to prevent the victimized devices from being taken over.
“Pink raced with the vendor to retain control over the infected devices, while vendor made repeated attempts to fix the problem, the bot master noticed the vendor’s action also in real time, and made multiple firmware updates on the fiber routers correspondingly,” the researchers said in an analysis published last week following coordinated action taken by the unspecified vendor and China’s Computer Network Emergency Response Technical Team/Coordination Center (CNCERT/CC).
Interestingly, Pink has also been found adopting DNS-Over-HTTPS (DoH), a protocol used for performing remote Domain Name System resolution via the HTTPS protocol, to connect to the controller specified in a configuration file that’s delivered either via a GitHub or Baidu Tieba as well as a built-in domain name hard-coded into some of the samples.
More than 96% of the zombie nodes part of the “super-large-scale bot network” were located in China, Beijing-based cybersecurity company NSFOCUS noted in an independent report, with the threat actor breaking into the devices to install malicious programs by taking advantage of zero-day vulnerabilities in the network gateway devices. Although a significant chunk of the infected devices has since been repaired and restored to their previous state as of July 2020, the botnet is still said to be active, comprising about 100,000 nodes.
With nearly 100 DDoS attacks having been launched by the botnet to date, the findings are yet another indication as to how botnets can offer a powerful infrastructure for bad actors to mount a variety of intrusions. “Internet of Things devices have become an important goal for black production organizations and even advanced persistent threats (APT) organizations,” NSFOCUS researchers said. “Although Pink is the largest botnet ever discovered, it will never be the last one.”
To read the original article:
https://thehackernews.com/2021/11/researchers-uncover-pink-botnet-malware.html