In early 2021, RiskIQ first detected a new phishing campaign targeting PayPal. The campaign, authored by an actor calling themself “Vagabon,” looks to collect PayPal login credentials and complete credit card information from the victim.
The kit doesn’t display many unique characteristics and is a textbook example of a “Frankenstein” kit. In this increasingly popular trend, threat actors piece together new phish kits from modular, free, or readily available kits and services.
The Vagabon Page
The Vagabon phishing page is a fake PayPal login screen. The page has a simple design with little branding information – just a “Log in to your PayPaI account” (note a capital “I” replaced the lower case “L” in PayPal in the title bar).
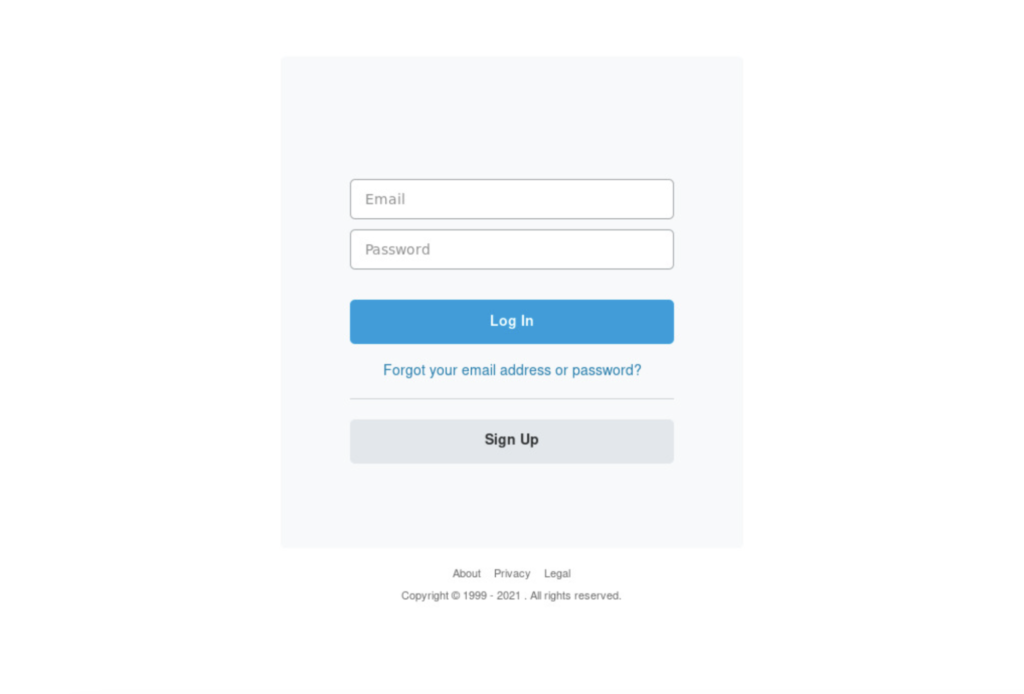
The Vagabon “PayPaI” phishing page.
In the response body of the phishing page, the characters “PayPa” are rendered using HTML entity characters followed by the capital “I.” This could be a technique to evade detection by researchers and analysts by not directly spelling “PayPal” within the response body contents.
The phishing page was hosted on payplchhkin[.]org and registered with DreamHost. Three other domains redirect traffic to the page, which you can see in RiskIQ’s threat intelligence portal.
Once a user falls victim to the sign-in phish, the Vagabon kit sends the user to a page requesting additional personal and credit card information, all of which gets pulled together for exfiltration to the attackers’ email.
RiskIQ has yet to observe an example of this specific phishing lure, but our researchers suspect it’s a phishing email and link that redirects victims to the fake PayPal login page.
The Vagabon Kit
The Vagabon kit contains bits and pieces of other known, familiar phish kits, a “Frankenstein” technique that has become increasingly popular. Each of its functions is typical of many of the most popular and effective kits across the threat landscape.
The Vagabon kit contains files written in four different languages: English, Spanish, French, and Arabic. Predominantly, files are English and Spanish or English and Arabic. However, some contain three or four languages, depending on the file function and the need to recall other foreign language files or functions.
The Vagabon kit, like many modern phish kits, contains code specific to blocking known research companies and common user agents. This code can be found within the .htaccess file as well as a bots.php file.
The Vagabon PayPal kit will execute various processes, such as leveraging a user’s IP geographic information to set the language and parameters for data validation as well as the exfiltration email address. The kit uses imported lang.php and info.php files to manage these processes.
Following the initial PayPal username and password theft, the kit has a flow for further data theft, moving on to pages for account information and credit card data.
Once the victim enters PayPal credentials, personal information, and credit card information, they redirect to the official PayPal website, which, to them, may seem like a perfectly legitimate place to end up. The attacker will then receive a “VagabonSpam” email containing all victim data points via the done.php file.
Scale Your Defenses to Tackle Frankenstein Kits
Phish kits constantly evolve and reconfigure to suit the individual needs of threat actors or evade detection. Knowing how these kits change – including knowing which elements they patch together from other kits across the web.
RiskIQ has used the Vagabon phish kit and the shared code found in other kits to improve our detection of phishing infrastructure across the globe. While the specific domains mentioned within our kit analysis are not currently active, the research has allowed us to recognize similar and identical code in compromised domains and point us toward other nefarious infrastructures. As our observations of amalgamated phish kits continue to grow, our ability to thwart phishing attacks by both sophisticated kit authors and amateur copycats does.
To read the original article:
https://www.riskiq.com/blog/external-threat-management/vagabon-kit-frankenstein-phishing/



