Before cybercriminals shifted heavily into ransomware, there was banking malware: sophisticated programs designed to collect login credentials and intervene in transactions.
That type of malware, though less prominent than ransomware, is still lurking around. And researchers with Mexico-based Metabase Q, a cybersecurity services company, have seen a notorious type of banking malware known as Dridex recently appear in Mexico.
Dridex emerged around 2012 and was an improvement upon two other types of banking malware, Bugat and Cridex, according to the U.S. Cybersecurity & Infrastructure Security Agency (CISA). It was often distributed through phishing emails with malicious attachments.
Once a computer is infected, Dridex can capture login credentials, but that’s just one of many features. It can detect when someone is logging onto a banking website and inject other malware or keylogging software.
It also has a link to ransomware. CISA writes that ransomware known as BitPaymer or Friedex have essentially the same mechanics as Dridex but the former two encrypt data while Dridex extracts it.
Also notable is that another type of ransomware known as Locky was distributed by the same botnet as Dridex around 2015 and 2016, the height of the banking malware era. Check Point, a security company, noted last year that Dridex was being used to distribute two types of ransomare: BitPaymer and DoppelPaymer.
Compromised Website
Metabase Q noticed three Dridex campaigns in Mexico starting in April of this year, writes José Zorrilla of Metabase Q’s Offensive Security Team, Ocelot, in a blog post.
The hosting and distribution point for Dridex was the website of Odette Carolina Lastra García, who is a representative for the Green Party (Partido Verde Ecologista de México) in the Congress of the state of Tabasco. Her website may have been vulnerable to compromise and was used to pass on Dridex, Zorrila writes. The site was suspended around mid-October.
Zorilla writes that there were three observed campaigns. In April, phishing emails with Dridex were sent around the world that lead to a version of Dridex placed on Lastra García’s website.
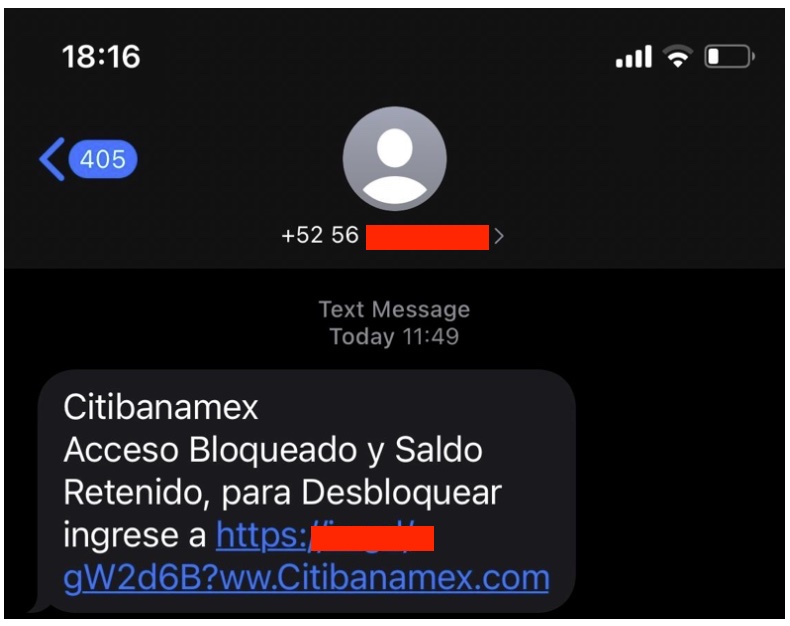
In August, deceptive SMS messages made the rounds that purported to come from the bank Citibanamex. Those messages contained a link that redirected to Lastra García’s infected website.
There was also a third ruse using the “SocGholish” framework. SocGholish uses several types of social engineering frameworks to try to entice people to download a bogus software update, which is actually a remote access trojan. Those tricks have included fake browser updates for Chrome or Firefox, but attackers are keeping up with the times and have an attack framework that spoofs a Microsoft Teams update, according to this post from Menlo Security.
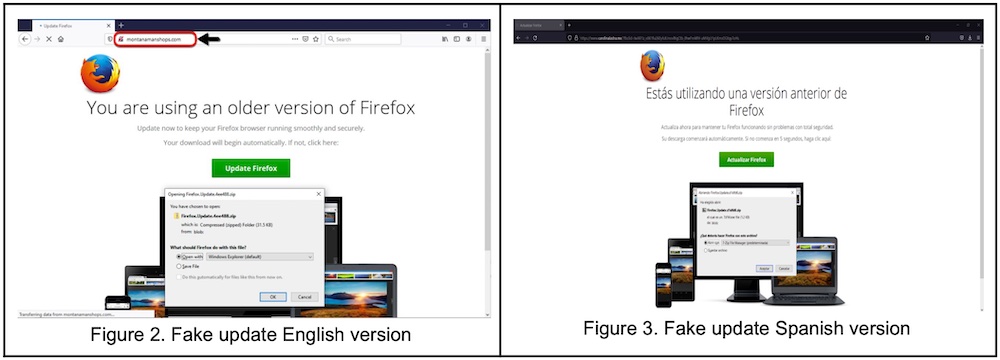 Screenshots of how SocGholish tries to trick a victim into downloading malware. (Source: Metabase Q)
Screenshots of how SocGholish tries to trick a victim into downloading malware. (Source: Metabase Q)
Zorilla writes that in the Mexico attacks, SocGholish uses legitimate remote monitoring software called NetSupport Manager to take control of a victim’s computer, the first time that has been identified in Mexico.
What’s been observed in Mexico is best classified as some of the traditional ways malware is distributed. One of relative of Dridex, known as DoppelDridex, has been seen hosted on Slack and Discord chat services.
Evil Corp
U.S. authorities have long had Dridex in their sights. The U.S. Treasury Department announced sanctions in December 2019 against what it alleged is a Russia-based cybercriminal organization calling itself Evil Corp, which is also linked to several types of ransomware and Dridex.
The department said that Evil Corp had used Dridex to infect computers and harvest login credentials from banks and financial institutions in 40 countries, causing more than $100 million in losses. The group is alleged to have also has run campaigns with the WastedLocker and PayloadBin ransomwares.
Also in December 2019, the Justice Department unsealed criminal charges against Maksim V. Yakubets, of Moscow, and Igor Turashev, from Yoshkar-Ola, Russia.
Both were charged with conspiracy, computer hacking, wire fraud and bank fraud related to the distribution of Dridex, Bugat and Cridex. Yakubets was also charged with conspiracy to commit bank fraud related to Zeus, another notable banking trojan. The Treasury Department also alleged that Yakubets also worked for the Russian government, aiding its cyber efforts.
Evil Corp went through an apparent rebrand earlier this year apparently in a bid to avoid sanctions. It’s technically illegal for organizations infected by ransomware to pay a ransom to a group under sanction (see Evil by a Different Name: Crime Gang Rebrands Ransomware).
Metabase Q believes the Mexico attacks could be linked with Evil Corp, and if so, shows how cybercriminals will continue to look for new markets albeit with old tricks.
To read the origianal article:
https://www.bankinfosecurity.com/dridex-banking-malware-turns-up-in-mexico-a-17879