A Mirai-based botnet called ‘Moobot’ is spreading aggressively via exploiting a critical command injection flaw in the webserver of many Hikvision products.
Hikvision is a state-owned Chinese manufacturer of surveillance cameras and equipment that the US government sanctioned due to human rights abuse.
This vulnerability is tracked as CVE-2021-36260 and can be exploited remotely by sending specially crafted messages containing malicious commands.
Hikvision fixed the flaw back in September 2021 with a firmware update (v 210628), but not all users rushed to apply the security update.
Fortinet reports that Moobot is leveraging this flaw to compromise unpatched devices and extract sensitive data from victims.
The infection process
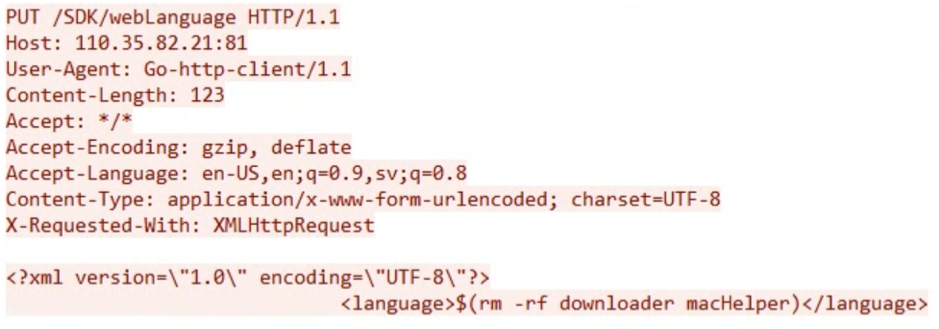
The exploitation of the flaw is fairly simple, given that it doesn’t require authentication and can be triggered by sending a message to a publicly exposed vulnerable device.
Source: Fortinet
Among the various payloads that leverage CVE-2021-36260, Fortinet found a downloader masked as “macHelper,” which fetches and executes Moobot with the “hikivision” parameter.
The malware also modifies basic commands like “reboot” so that they do not function properly and will prevent the administrator from rebooting the compromised device.
A new spin of Mirai
Fortinet’s analysts have spotted common points between Moobot and Mirai, such as the data string used in the random alphanumeric string generator function.
Moreover, Moobot features some elements from Satori, a different Mirai variant whose author was arrested and sentenced in the summer of 2020.
Similarities with Satori include:
- Using a separate downloader.
- The forking of the “/usr/sbin*” process.
- Overwriting the legitimate “macHelper” file with the Moobot executable.
It is essential to underline that this is not the first time Moobot was spotted in the wild, as researchers at Unit 42 first discovered it in February 2021.
However, the fact that the botnet is still adding new CVEs indicates that it is being actively developed and enriched with new targeting potential.
Enlisting you into a DDoS army
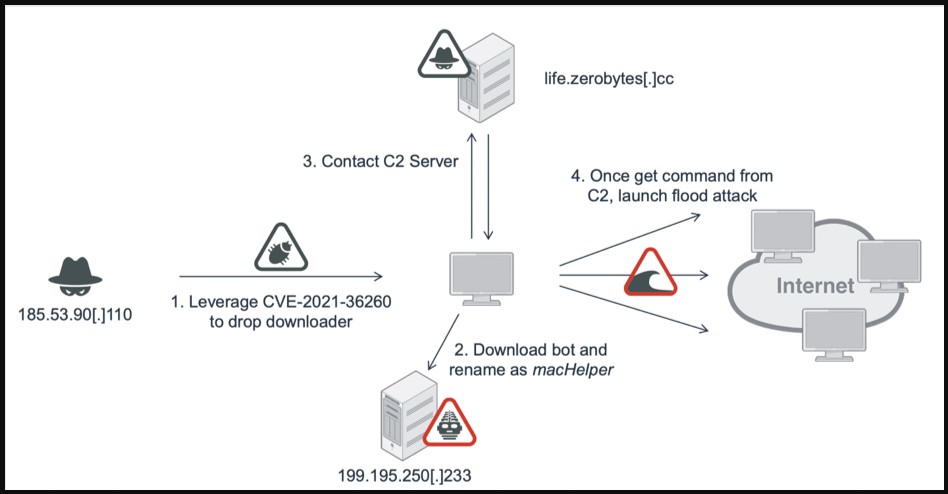
The goal of Moobot is to incorporate the compromised device into a DDoS swarm.
The C2 sends an SYN flood command along with the target IP address and port number to attack.
Source: Fortinet
Other commands that the C2 server may send include 0x06 for UDP flood, 0x04 for ACK flood, and 0x05 for ACK+PUSH flood.
By looking into the captured packet data, Fortinet could track down a Telegram channel that started offering DDoS services last August.
Having your device enlisted in DDoS swarms results in increased energy consumption, accelerated wear, and causes the device to become unresponsive.
The best way to protect your IoT devices from botnets is to apply available security updates as soon as possible, isolate them in a dedicated network, and replace the default credentials with strong passwords.
To read the original article:



