An Android banking trojan targeting Itaú Unibanco, a large financial services provider in Brazil with 55 million customers globally, has deployed an unusual trick to spread to devices.
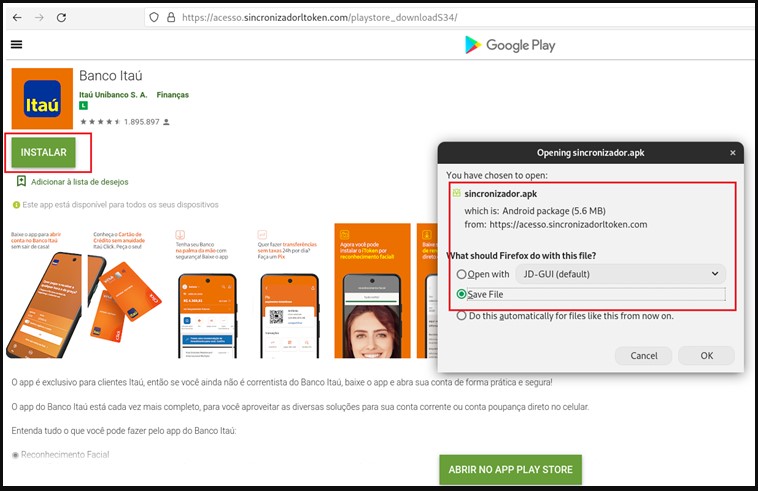
The actors have set up a page that looks very close to Android’s official Google Play app store to trick visitors into thinking they are installing the app from a trustworthy service.
Source: Cyble
The malware pretends to be the official banking app for Itaú Unibanco and features the same icon as the legitimate app.
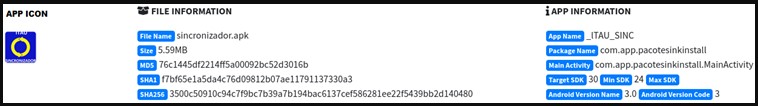
If the user clicks on the “Install” button, they are offered to download the APK, which is the first sign of the scam. Google Play Store apps are installed through the store interface, never asking the user to download and install programs manually.
Source: Cyble
Hijacking the actual app
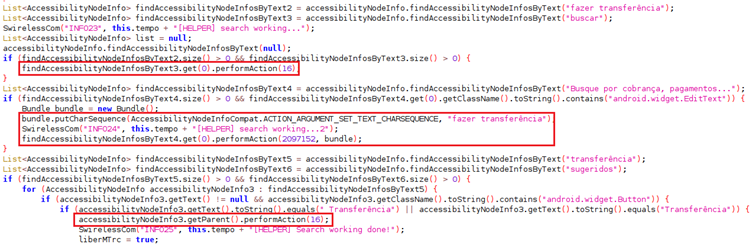
Researchers at Cyble analyzed the malware, finding that upon execution, it attempts to open the real Itaú app from the actual Play Store.
If that succeeds, it uses the actual app to perform fraudulent transactions by changing the user’s input fields.
Source: Cyble
The app doesn’t request any dangerous permissions during installation, thus avoiding raising suspicious or risking detection from AV tools.
Instead, it aims to leverage the Accessibility Service, which is all that’s needed by mobile malware to bypass all security on Android systems.
As a recent report by Security Research Labs explains, we are dealing with an Android malware Accessibility abuse pandemic right now, and Google is yet to plug the targeted weak spot.
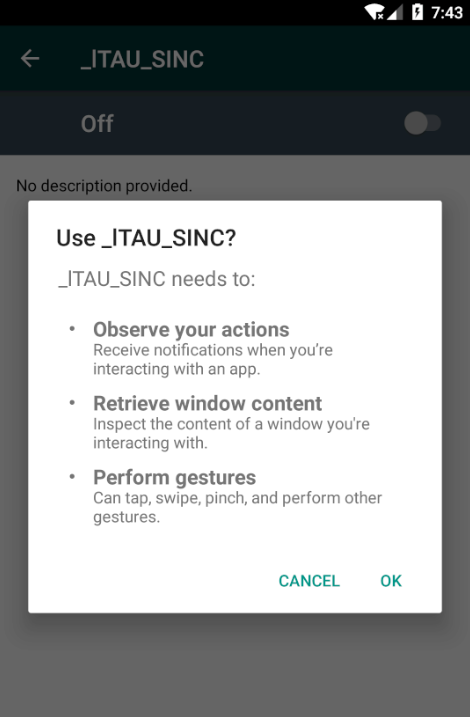
As such, only the user has the chance to spot the signs of abuse and stop the malware before it gets a chance to perform destructive actions on the device.
Source: Cyble
These signs come in the form of the app requesting permission to perform gestures, retrieve window content, and observe user actions.
The websites used to distribute the malicious APKs have been reported and taken offline for now, but the actors may return through different domains.
Use the real banking apps
If you want to enjoy the convenience of mobile e-banking, make sure to install the app from the bank’s official website or the Google Play Store.
Moreover, apply updates on the app as soon as they become available and use an AV tool from a reputable vendor.
To ensure maximum account security, use a strong password and enable multi-factor authentication on the app.
If you need to install APKs from outside the store, carefully scrutinize their permissions requests during and after installation.
Finally, regularly check and ensure that Google Play Protect is enabled on your Android device.
To read the original article:



