An ongoing ZLoader malware campaign has been uncovered exploiting remote monitoring tools and a nine-year-old flaw concerning Microsoft’s digital signature verification to siphon user credentials and sensitive information.
Israeli cybersecurity company Check Point Research, which has been tracking the sophisticated infection chain since November 2021, attributed it to a cybercriminal group dubbed MalSmoke, citing similarities with previous attacks.
“The techniques incorporated in the infection chain include the use of legitimate remote management software (RMM) to gain initial access to the target machine,” Check Point’s Golan Cohen said in a report shared with The Hacker News. “The malware then exploits Microsoft’s digital signature verification method to inject its payload into a signed system DLL to further evade the system’s defenses.”
A banking trojan at its core, ZLoader has been employed by many an attacker to steal cookies, passwords, and other private information from victims’ machines, not to mention gaining notoriety for acting as a distribution framework for Conti ransomware, according to an advisory published by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) in September 2021.
The campaign is said to have claimed 2,170 victims across 111 countries as of January 2, 2022, with most of the affected parties located in the U.S., Canada, India, Indonesia, and Australia. It’s also notable for the fact that it wraps itself in layers of obfuscation and other detection-evasion methods to elude discovery and analysis.
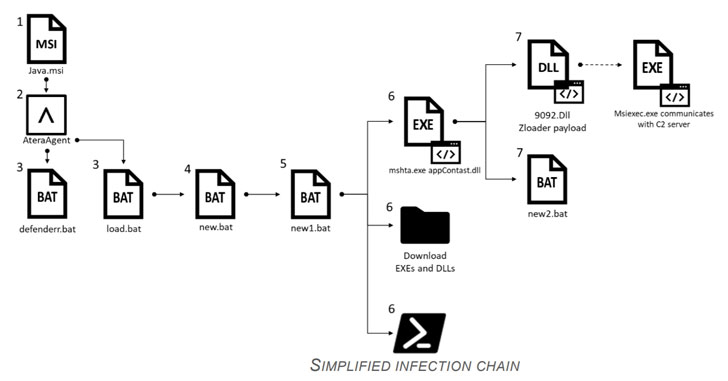
The attack flow commences with tricking users into installing a legitimate enterprise remote monitoring software called Atera, using it to upload and download arbitrary files as well as execute malicious scripts. However, the exact mode of distributing the installer file remains unknown as yet.
One of the files is used to add exclusions to Windows Defender, while a second file proceeds to retrieve and execute next-stage payloads, including a DLL file called “appContast.dll” that, in turn, is used to run the ZLoader binary (“9092.dll”).
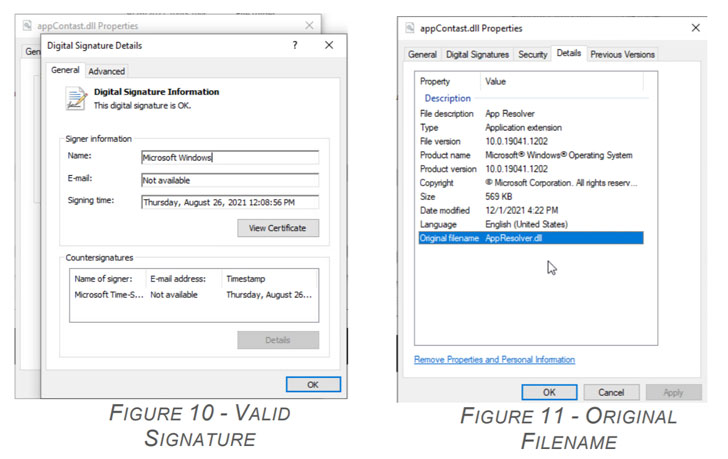
What stands out here is that appContast.dll is not only signed by Microsoft with a valid signature, but also that the file, originally an app resolver module (“AppResolver.dll”), has been tweaked and injected with a malicious script to load the final-stage malware.
This is made possible by exploiting a known issue tracked as CVE-2013-3900 — a WinVerifyTrust signature validation vulnerability — that allows remote attackers to execute arbitrary code via specially crafted portable executables by making subtle enough changes to the file without revoking the validity of the digital signature.
Although Microsoft addressed the bug in 2013, the company revised its plans in July 2014 to no longer “enforce the stricter verification behavior as a default functionality on supported releases of Microsoft Windows” and made it available as an opt-in feature. “In other words, this fix is disabled by default, which is what enables the malware author to modify the signed file,” Cohen said.
“It seems like the ZLoader campaign authors put great effort into defense evasion and are still updating their methods on a weekly basis,” Check Point malware researcher, Kobi Eisenkraft, said, urging users to refrain from installing software from unknown sources and apply Microsoft’s strict Windows Authenticode signature verification for executable files.
To read the original article:
https://thehackernews.com/2022/01/new-zloader-banking-malware-campaign.html