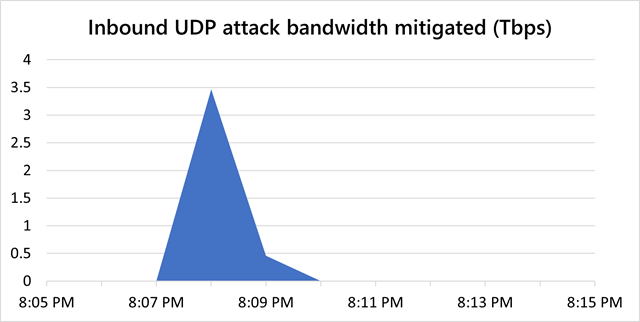
Microsoft says its Azure DDoS protection platform mitigated a massive 3.47 terabits per second (Tbps) distributed denial of service (DDoS) attack targeting an Azure customer from Asia in November.
Two more large size attacks followed this in December, also targeting Asian Azure customers, a 3.25 Tbps UDP attack on ports 80 and 443 and a 2.55 Tbps UDP flood on port 443.
“In November, Microsoft mitigated a DDoS attack with a throughput of 3.47 Tbps and a packet rate of 340 million packets per second (pps), targeting an Azure customer in Asia. We believe this to be the largest attack ever reported in history,” said Alethea Toh, an Azure Networking Product Manager.
“This was a distributed attack originating from approximately 10,000 sources and from multiple countries across the globe, including the United States, China, South Korea, Russia, Thailand, India, Vietnam, Iran, Indonesia, and Taiwan.”
The 15 minutes attack used multiple attack vectors for UDP reflection on port 80, including:
- Simple Service Discovery Protocol (SSDP),
- Connection-less Lightweight Directory Access Protocol (CLDAP),
- Domain Name System (DNS),
- and Network Time Protocol (NTP)
Previous record-breaking publicly reported DDoS attacks were a 21.8 million requests per second (rrps) application layer assault that hit the Russian internet giant Yandex in August and a 2.3 Tbps volumetric strike detected by Amazon Web Services Shield during Q1 2020.
Google Security Reliability Engineer Damian Menscher also revealed two years ago that Google mitigated a 2.54 Tbps DDoS in 2017.
“Largest attack ever reported in history”
The November 3.47 Tbps attack was the largest one the company had to face to date (and likely ever recorded), after previously reporting that it mitigated another record 2.4 Tbps attack targeting a European Azure customer during late August.
Microsoft saw a rise in attacks that lasted longer than an hour in the second half of 2021, while multi-vector attacks such as the record one mitigated in November were prevalent.
These more prolonged DDoS attacks usually come as a sequence of short-lived, repeated burst attacks quickly ramping up (in seconds) to terabit volumes.
“Gaming continues to be the hardest hit industry. The gaming industry has always been rife with DDoS attacks because players often go to great lengths to win,” Toh added.
“The concentration of attacks in Asia can be largely explained by the huge gaming footprint10, especially in China, Japan, South Korea, Hong Kong, and India, which will continue to grow as the increasing smartphone penetration drives the popularity of mobile gaming in Asia.”
Microsoft also defended customers against new TCP PUSH-ACK flood attacks (dominant in the East Asia region) during the 2021 holiday season.
“We observed a new TCP option manipulation technique used by attackers to dump large payloads, whereby in this attack variation, the TCP option length is longer than the option header itself,” Toh said.
To read the original article:



