A politically motivated advanced persistent threat (APT) group has expanded its malware arsenal to include a new remote access trojan (RAT) in its espionage attacks aimed at Indian military and diplomatic entities.
Called CapraRAT by Trend Micro, the implant is an Android RAT that exhibits a high “degree of crossover” with another Windows malware known as CrimsonRAT that’s associated with Earth Karkaddan, a threat actor that’s also tracked under the monikers APT36, Operation C-Major, PROJECTM, Mythic Leopard, and Transparent Tribe.The first concrete signs of APT36’s existence appeared in 2016 as the group began distributing information-stealing malware through phishing emails with malicious PDF attachments targeting Indian military and government personnel. The group is believed to be of Pakistani origin and operational since at least 2013.
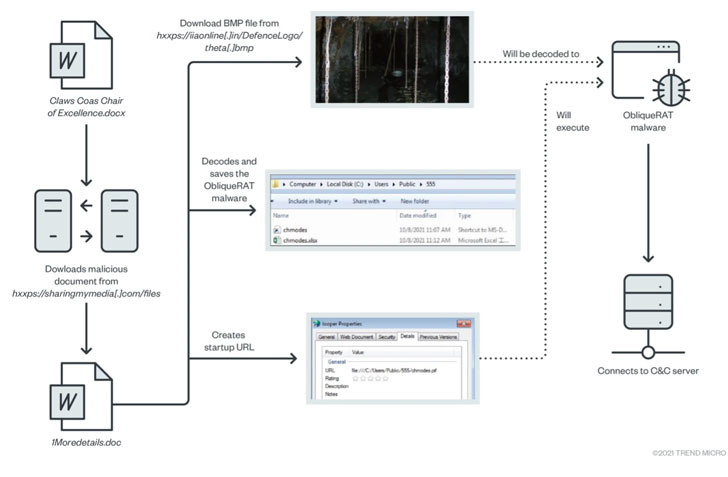
The threat actor is also known to be consistent in its modus operandi, with the attacks predominantly banking on social engineering and a USB-based worm as entry points. Among common elements in the group’s arsenal is a Windows backdoor called CrimsonRAT that allows the attackers extensive access to compromised systems, although recent campaigns have evolved to deliver ObliqueRAT.CrimsonRAT is fashioned as a .NET binary whose main purpose is to obtain and exfiltrate information from targeted Windows systems, including screenshots, keystrokes, and files from removable drives, and upload them to the attacker’s command-and-control server.
The new addition to its toolset is yet another custom Android RAT that’s deployed by means of phishing links. CapraRAT, which is disguised as a YouTube app, is said to be a modified version of an open-source RAT called AndroRAT and comes with a variety of data exfiltration functions, including the ability to harvest victims’ locations, phone logs, and contact information. This is far from the first time the hacking group has used Android RATs. In May 2018, human rights defenders in Pakistan were targeted by Android spyware named StealthAgent to intercept phone calls and messages, siphon photos, and track their whereabouts.Then in 2020, attack campaigns mounted by Transparent Tribe involved leveraging military-themed lures to drop a modified version of the AhMyth Android RAT that masqueraded as a porn-related app and a fake version of the Aarogya Setu COVID-19 tracking app.
To mitigate such attacks, users are advised to watch out for unsolicited emails, avoid clicking on links or downloading email attachments from unknown senders, install apps only from trusted sources, and exercise caution when it comes to granting permissions requested by the apps.To read the original article:
https://thehackernews.com/2022/02/new-caprarat-android-malware-targets.html